It seems I’m reading this question more and more: “I’m an Administrator on a Windows Vista box, but I can’t run program X with administrator rights”.
I’ll try to explain this quickly and simply, omitting a lot of details (if there is enough interest, I’ll make a follow-up post).
The cause of this program’s behavior is simple: restricted tokens. A token is a Windows kernel object that represents a user with all his privileges and group-memberships. The token is created when a user is login on, and is associated with all programs started by that user (i.e. processes). The Windows kernel uses the token to decide if the process is granted access to the securable objects it tries to access.
A restricted token is a special token: it’s a token that represents only a part of what a user is allowed to do. Some privileges and permissions have been removed or denied (restricted). Restricted tokens exists since Windows 2000, but as a user, you weren’t really confronted with them until Windows Vista. Since Windows Vista, restricted tokens are used to run most user programs, in stead of the normal (unrestricted) tokens. In Windows Vista, when an administrator is login on, 2 tokens are created: the normal token (with all administrative rights) and a restricted token. For security reasons, most programs are started with the restricted token. And that’s why some programs don’t run as you expect, because they need more privileges and permissions than the restricted token is giving them.
UAC decides if a program is started with the unrestricted token or the restricted token. There are several rules that guide UAC in its decision process between the 2 tokens, the application manifest is one source of information used by the UAC rules. The manifest is an XML file stored as a resource inside a PE file, and it can contain information about the execution level it needs to run correctly. If an application needs administrative rights, the developer should add an requireAdministrator value to the manifest file, so that the UAC uses the unrestricted token. If your application is missing this manifest, chances are that UAC will make the wrong decision and run the program with the wrong token.
As a user, you can also instruct UAC to use the unrestricted token: right-click the program you want to start and select “Run as administrator”.
If you often need to run the same program with administrative rights and UAC systematically makes the wrong decision about the token to use, create a shortcut to the program and check the “Run as administrator” toggle in the advanced tab:
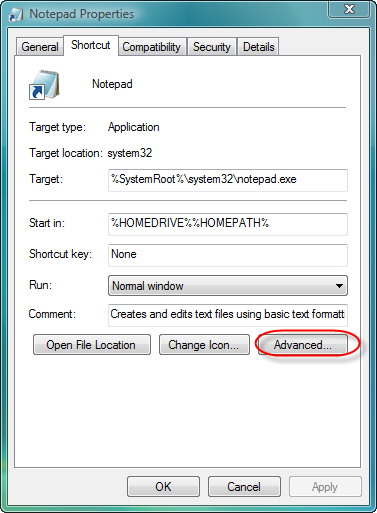

Another way to achieve this is to add (or update) a manifest to the executable file with a resource editor.
I’ve noticed that tokens in Vista also seem to control the interaction of activities between applications.
For example, on my XP Home system, I blog using two applications: Firefox (3.0 nightlies) and Windows Live Writer.
On this platform I can drag and drop links and text from Firefox directly into WLW with no issues.
On our Vista (Home Premium) laptop, I cannot do this unless I launch both WLW and Firefox with the “Run as Administrator” method.
My Logitech wireless mouse has a highly-customizable scroll-click wheel which I have set to copy/paste actions. On XP I can copy/paste anywhere into anything. On Vista the same mouse and software refused to copy/paste between different applications until I set the auto-start Logitech process to launch as a scheduled task with “Run as Administrator” enabled. Took me a while to work that one out!
I actually like and think UAC is a good thing, but for many users, especially those who have always run under the administrator group rights, these extra levels of token control take some getting used to. Once the concept is understood things work good.
I do find it still confusing when deciding if I should install an application with “run as administrator” or not. Generally for security applications I do so, and for “standard” applications I do not. Not sure. I would assume the installer would handle that, but from what I’ve seen and experienced, sometimes with Vista you must install some apps that way, but it takes trial and error (and review of forums) to get it worked out.
Any ideas or guidance on this?
Thanks for the awesome posts!
Comment by Claus Valca — Monday 9 June 2008 @ 0:33
I experienced this on my XP system where I use a non-admin account. Some applications require administrative access, so I would start them with a runas command with administrator credentials. And then I wouldn’t be able to drag and drop between this application and explorer. To be able to drag and drop, I needed to start another explorer application (like 2xexplroer) with administrator credentials, and then I could drag and drop between these two applications.
I don’t think this is a Vista or UAC problem, but is linked to drag and drop OLE.
Now for installing programs on my Vista box, I started to work like this:
– if the program needs to be installed, I’ll first try to find a portable version of the program and start to use this
– if there is no portable version, after having tested the program in a VM, I’ll install it on my Vista box, temporarily logging on with the administrator account.
Comment by Didier Stevens — Tuesday 10 June 2008 @ 10:59
You wrote: In Windows Vista, when an administrator is login on, 2 tokens are created: the normal token (with all administrative rights) and a restricted token.
This works against the restricted token:
WindowsIdentity user = WindowsIdentity.GetCurrent();
WindowsPrincipal princ = new WindowsPrincipal(user);
Console.WriteLine(“Is Administrator = {0}”, princ.IsInRole(WindowsBuiltInRole.Administrator));
QUESTION: How can I enumerate the “normal token” SID’s ?
Comment by SteveK — Wednesday 22 October 2008 @ 8:36
Your C# code works with the restricted token because UAC gave it the restricted token.
Start your C# code with “Run as administrator”, accept the elevation prompt, and your code will run with the normal administrator token.
Comment by Didier Stevens — Wednesday 22 October 2008 @ 20:22
[…] not talking about targeted attacks), restrict the user rights. Windows Vista and later versions do this for you with UAC, even if you’re an […]
Pingback by Preventing Malicious Documents from Compromising Windows Machines « Didier Stevens — Sunday 27 September 2009 @ 13:33
It would seem Windows 7 no longer uses restricted tokens for UAC: In my unelevated token (“Medium” integrity level, whereas the elevated one is “High”), The Administrators group still becomes deny-only, but IsTokenRestricted() now returns false, whereas it returned true on Windows Vista.
Comment by Fred — Friday 25 September 2015 @ 9:58