ExtractScripts is another one of my little tools I use to analyze malware.
Tuesday 26 June 2007
Wednesday 20 June 2007
UserAssist Q&A
I was a speaker at the local ISSA chapter last Monday. My talk explained how to use my UserAssist tool for forensic analysis. The audience had great questions for me at the Q&A, some of which I want to share here.
Does switching to the “Classic Start Menu” prevent the logging of data in the UserAssist registry keys?
No, it doesn’t. When you use the classic start menu (the start menu from Windows NT & 2000, without a frequently used programs pane), Windows explorer still continues to monitor and log the programs you execute. When you switch back to the “modern” start menu, you’ll see several of the programs you recently used in the frequently used programs pane.
Does disabling the Active Desktop prevent the logging of data in the UserAssist registry keys?
No, it doesn’t. In fact, I use the following litmus test to know if starting a program is recorded in the UserAssist keys: did a user perform the action through Windows explorer? If a user did, then the action is logged.
The only trick I know to permanently disable the UserAssist keys is this one:
- add a new subkey “Settings” under the “UserAssist” key
- add a new DWORD value “NoLog” and set it to one.
My UserAssist tool allows you to toggle this setting via a simple menu command.
One audience member asked me if I was really sure that using a mandatory user profile (NTUSER.MAN) implied that the UserAssist registry keys where not persisted.
I promised him that I would test it, and I must admit that I was wrong.
A mandatory user profile is a profile that the user can change, but the changes are not saved when the user logs out.
This is how I tested the UserAssist tool with a mandatory user profile:
- a domain controller
- a member workstation
- a domain user with the profile path set to a share on the DC
- renaming NTUSER.DAT to NTUSER.MAN
- log on to the workstation with the domain user account
- start some programs
- analyse the profiles
I discovered that the NTUSER.MAN file in the local copy of the profile (file NTUSER.MAN in c:\document and settings\user on the workstation) had been modified, and that the UserAssist keys listed the program I had executed. As expected, the NTUSER.MAN file on the DC in the roaming user profile was not modified. And when I logged on to the workstation a second time, the local profile was overwritten with the mandatory profile, as expected.
So you can use the NTUSER.MAN file in a forensic investigation, but some restrictions apply:
- use the local copy, not the file hosted on the DC (in fact, you should compare the UserAssist entries from both files, because some entries in the UserAssist keys might come from the original NTUSER.MAN file)
- make sure to grab a copy before the user logs on again, otherwise the file will be overwritten (you could try to recover it)
- entries in the UserAssist keys will pertain to the last session of the user, it is not a complete history of all the sessions (and remember restriction 1, comparing the profiles)
Raymond Chen has started a series of blog posts about the Start Menu’s frequently used programs. Keep in mind that he discusses the rules that govern the display and ranking of programs on the start menu, and not actually the rules for collecting the data (i.e. UserAssist keys). What he calls points is not the same as the counter in a UserAssist entry.
Monday 11 June 2007
Some e-voting observations
Last Sunday, we had federal elections here in Belgium. I’m glad to see that the electronic voting system I used is designed to minimize voter coercion.
The secret ballot prevents coercion (being forced to vote for a certain person or party): if the voter can’t produce evidence of how he voted, he can lie to the coercer about his vote without risk. Some political parties want to change the process of the secret electronic ballot and include a paper trail. This is not a good idea, it will make coercion much more effective, as the voter will have an official paper with his vote.
The ubiquitousness of mobile phones equiped with a camera gives coercers a new opportunity to require proof from the persons they are coercing. The coercer just has to instruct his victim to take a picture of his ballot. The Belgian electronic ballot is designed to prevent this. When you’ve casted your vote, you’ll see a screen like this one:

The 2 buttons at the bottom of the screen allow you to:
- left button: go back a screen and change your vote
- right button: confirm your vote
Once you have confirmed your vote, the next screen doesn’t display how you voted. So if one is coerced and has to deliver proof, one just has to take a picture of the vote one was coerced into, and then back out from the screen and change ones vote. The only workaround I see is for the coercer to demand a video of the complete voting process, in stead of a picture of the ballot.
I’ve made a video of my voting last Sunday, and it turned out to be rather difficult to do. First of all, I was standing very close to the screen and I clumsily managed to film only the bottom of the screen. Secondly, the brightness of the CRT screen (black letters on a white background) makes it very hard to read my ballot on the video. This could also be an anti-coercion mechanism, taking legible pictures of a white screen is very hard.
This is an advantage that our electronic ballot has over our paper ballot, it is more effective against voter coercion.
You can find a simulation of the Belgian electronic ballot here:
Tuesday 5 June 2007
OMG, My N800 is Infected!
I followed a link from a comment spam I had on my blog. Turns out my machine is infected:

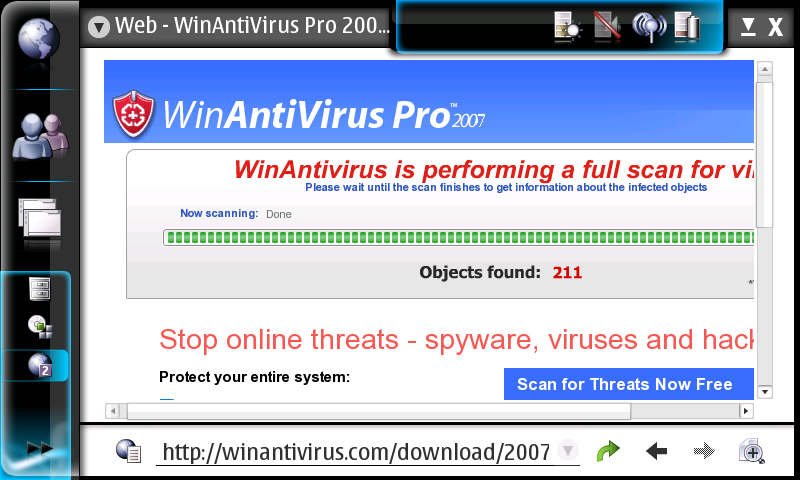
This is really disappointing, I didn’t expect my brand new Linux-based Nokia N800 to get infected so soon:
