Here is a set of free YouTube videos showing how to use my tools: Workshop Malicious Documents.
oledump.py is a program to analyze OLE files (Compound File Binary Format). These files contain streams of data. oledump allows you to analyze these streams.
Many applications use this file format, the best known is MS Office. .doc, .xls, .ppt, … are OLE files (docx, xlsx, … is the new file format: XML inside ZIP).
oledump has an embedded man page: run oledump.py -m to view it.
Run oledump on an .xls file and it will show you the streams:

The letter M next to stream 7, 8, 9 and 10 indicate that the stream contains VBA macros.
You can select a stream to dump its content:

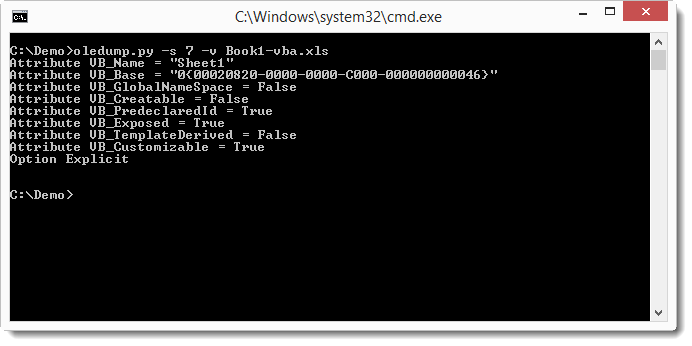
The source code of VBA macros is compressed when stored inside a stream. Use option -v to decompress the VBA macros:
You can write plugins (in Python) to analyze streams. I developed 3 plugins. Plugin plugin_http_heuristics.py uses a couple of tricks to extract URLs from malicious, obfuscated VBA macros, like this:
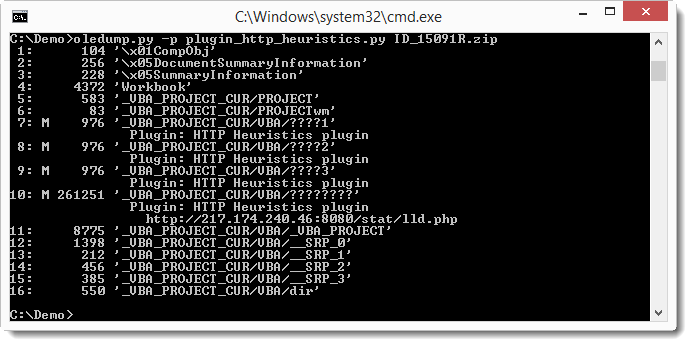
You might have noticed that the file analyzed in the above screenshot is a zip file. Like many of my analysis programs, oledump.py can analyze a file inside a (password protected) zip file. This allows you to store your malware samples in password protected zip files (password infected), and then analyze them without having to extract them.
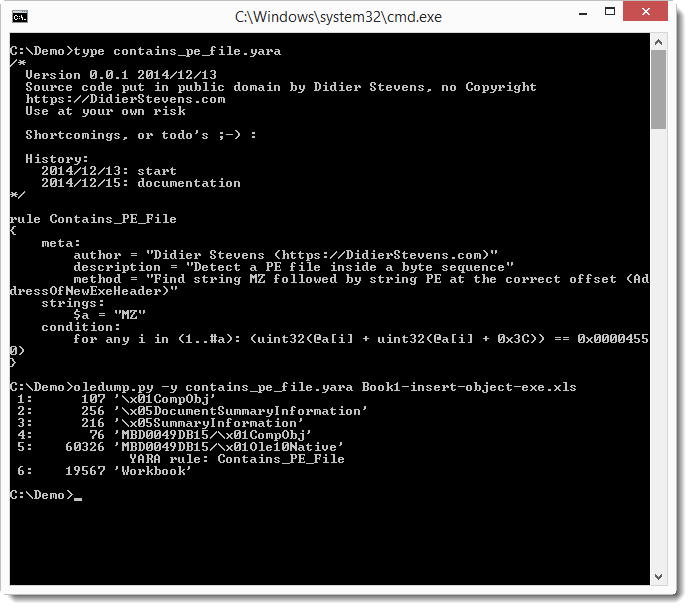
If you install the YARA Python module, you can scan the streams with YARA rules:
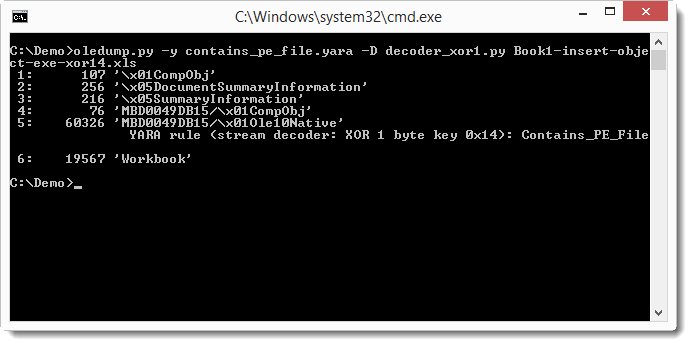
And if you suspect that the content of a stream is encoded, for example with XOR, you can try to brute-force the XOR key with a simple decoder I provide (or you can develop your own decoder in Python):
This program requires Python module OleFileIO_PL: http://www.decalage.info/python/olefileio
oledump_V0_0_75.zip (http)MD5: FB0F82B3B29883707A399B99C894EF08
SHA256: D357E48D827822D15C9C22C0B5204924FBA9FC59104818C9824AD149FE6F6249
Hi Didier, thank you for the wonderful tool!
Word macro’s are being used a lot recently for TorrentLocker, Dridex and now Rovnix distribution.
Hoping you might be able to take a look at some recent extracted word macro’s and possibly add plugin functionality to extract badness or better detect these URL’s ?
The URL obfuscation techniques used are quite varied…
http://pastebin.com/cDmn7tPW
http://pastebin.com/JwugYBbR
http://pastebin.com/fbyxcLCB
http://pastebin.com/iWmiG3Zg
http://pastebin.com/mNRC5PdL
Thanks!
Comment by Nullsec — Wednesday 7 January 2015 @ 8:49
Hi Didier, thank you for the wonderful tool!
Word macro’s are being used a lot recently for TorrentLocker, Dridex and now Rovnix distribution.
Hoping you might be able to take a look at some recent extracted word macro’s and possibly add plugin functionality to extract badness or better detect these URL’s ?
The URL obfuscation techniques used are quite varied…
http://pastebin.com/cDmn7tPW
http://pastebin.com/JwugYBbR
http://pastebin.com/fbyxcLCB
http://pastebin.com/iWmiG3Zg
http://pastebin.com/mNRC5PdL
Thanks!
Comment by digian — Wednesday 7 January 2015 @ 8:57
Did you test the latest version op plugin_http_heuristics? I decodes 4 of your samples.
Comment by Didier Stevens — Thursday 8 January 2015 @ 21:01
Thanks, plugin_http_heuristics works a treat,
PS. Could you plz delete previous duplicate post. =)
Comment by Anonymous — Monday 12 January 2015 @ 8:23
[…] files are actually .doc and therefore in OLE format. In that case one of the best tool available is oledump.py from Didier Stevens (also known for his PDF tools…but we will talk about that in an upcoming […]
Pingback by Word document analysis with oledump.py | SimonGaniere.ch — Monday 12 January 2015 @ 13:56
Is it possible to use the plugin_http_heuristics to export the macro as decoded so I can view what else it is doing besides just knowing that it calls to a specific IP address?
Comment by Greg Kelley — Tuesday 13 January 2015 @ 14:46
You don’t need a plugin for that. Just select the stream containing macros (using option -s) and use option-v to vies the VBA code.
Comment by Didier Stevens — Tuesday 13 January 2015 @ 14:48
I did, but then I get obscured code
Comment by Greg Kelley — Tuesday 13 January 2015 @ 14:56
I see. You want a deobfuscator, and you think plugin_http_heuristics does this but does not show you the deobfuscated code?
That’s not how the plugin works. It does not deobfuscate VBA code. It tries to deobfuscate strings.
Comment by Didier Stevens — Tuesday 13 January 2015 @ 19:18
[…] wrote a short guide using Python. If you want to take the simpler route, Didier Steven’s OLE Dump tool has a plug-in that will automatically decode and extract these URLs, as shown […]
Pingback by Dridex Banking Trojan Begins 2015 with a Bang - Palo Alto Networks BlogPalo Alto Networks Blog — Friday 16 January 2015 @ 23:45
[…] I converted Jim Clausing’s PEiD rules to YARA rules so that I can use them to detect executable code in suspect Microsoft Office Documents with my oledump tool. […]
Pingback by Converting PEiD Signatures To YARA Rules | Didier Stevens — Thursday 22 January 2015 @ 0:57
[…] oledump.py […]
Pingback by oledump With plugin_biff | Didier Stevens Videos — Friday 23 January 2015 @ 9:57
Here’s another new Dridex obfuscation mechanism (found in a Word document). Any possibility you could update the plugin_http_heuristics plugin?
http://pastebin.com/ag1cpB08
Thanks
John McCash
Comment by Anonymous — Wednesday 4 February 2015 @ 16:08
Do you the MD5 of the sample John?
Comment by Didier Stevens — Wednesday 4 February 2015 @ 18:14
I believe it was cd5fdb7574010fd23f9501523fdc2aa4. The filename was invoice4780242454.doc, and the included download address was hxxp://www[.]stoneledgepens[.]com/blog/wp-content/uploads/vv.exe.
Comment by Anonymous — Friday 6 February 2015 @ 20:56
Didier, great tool! I found a possible error in the script. 3fec5921bd1f9a2cca4f5c707a51aded and 10b7af49f09c882f5b16c87f31353bc4 show “string index out of range” errors. In the Decompress method, you check “while len(remainder) != 0” but in the DecompressChunk method, you check the first 2 bytes. Let me know if you need to me to send you the files.
Comment by Jose Ole — Monday 23 February 2015 @ 14:31
Also, 02a0f412b52324d10635f9562a5c24fc and 4a2d6df0a23911188c3a00c7bfc025f9 are examples of “math domain error” on the first line of the OffsetBits method. len(data) is 0 at that point.
Comment by Jose Ole — Monday 23 February 2015 @ 14:46
@Jose I had a look, that first file is corrupted. That’s why decompressing the macro fails.
Comment by Didier Stevens — Monday 23 February 2015 @ 20:15
@Jose Seems the 4 files are corrupted.
Comment by Didier Stevens — Monday 23 February 2015 @ 20:57
@Didier Thanks for taking a look. If I change “len(remainder) != 0” to “len(remainder) > 1” the first two files are able to continue on without error and even finds an embedded executable in stream 21 of the first and a macro of interest in stream 13 in the other.
Comment by Jose Ole — Monday 23 February 2015 @ 21:21
@Jose Yes, I’ll make a new version to handle the error.
Comment by Didier Stevens — Monday 23 February 2015 @ 21:23
Great. Thanks for your help.
Comment by Jose Ole — Monday 23 February 2015 @ 21:27
For the math domain error, I just changed the “else” on the line before “numberOfOffsetBits = OffsetBits(decompressedChunk)” to “elif len(decompressedChunk) > 0”
Comment by Jose Ole — Monday 23 February 2015 @ 21:33
[…] You can find oledump.py here. […]
Pingback by oledump And Yet Another XML (Bis) | Didier Stevens Videos — Sunday 29 March 2015 @ 0:07
[…] It was too tempting to make some manual investigations. Using Didier Stevens’s tool oledump, I extracted the following […]
Pingback by Malicious MS Word Document not Detected by AV Software | /dev/random — Tuesday 7 April 2015 @ 18:27
Hi Didier, great tool! I have added a simple patch to 0.0.13 based on Rodel Medrez’s macrodump to extract all VBA macros in one go. I think it could be useful to everyone — do you think you could add this feature to the next version?
542a543,551
> def VBAdump(ole):
> for fname in ole.listdir():
> stream = ole.openstream(fname).read()
> if ‘\x00Attribut’ in stream:
> print PrintableName(fname)
> StdoutWriteChunked(SearchAndDecompress(stream))
> #print(‘%2d: %s %6d %s’ % (counter, IFF(‘\x00Attribut’ in stream, ‘M’, ‘ ‘), len(stream), PrintableName(fname)))
> return
>
897a907,910
> if options.VBAdump:
> VBAdump(ole)
> return
>
1155a1169
> oParser.add_option(‘-V’, ‘–VBAdump’, action=’store_true’, default=False, help=’attempt to dump all VBA macros’)
Comment by Tamas — Thursday 9 April 2015 @ 18:23
@Tamas Did you know that you can perform an operation on all streams by selecting all streams, like this: -s a
So to see all macros you give options -s a -v
Comment by Didier Stevens — Thursday 9 April 2015 @ 21:40
[…] new version of oledump (small bugfix and updated […]
Pingback by Update: oledump.py Version 0.0.14 | Didier Stevens — Monday 13 April 2015 @ 0:01
Thanks very much @Didier to get back to this. I did not know this option, however, I have tried and the problem with that is that it selects every streams not just the VBA ones. As a result we will see many “Error: unable to decompress” messages for the ones not compressed VBAs, and also I saw “VBA/dir” displayed in an unformatted way — which is not what I wanted. In the other hand your direction is better than mine. It would be nice to have “-sv” or “-sm” for selecting all VBA macros and maybe could extend this to “-sw” for word docs, “-sx” for xls, “-se” for embedded objects etc. Just few ideas 🙂
Comment by Tamas — Thursday 16 April 2015 @ 21:25
PS: What I was thinking is something like this:
$ diff oledump-0.0.14.py oledump-0.0.14p.py
1012,1014c1012,1018
< if options.select == 'a' or ('%s%d' % (prefix, counter)) == options.select:
< StdoutWriteChunked(DumpFunction(DecompressFunction(DecodeFunction(decoders, options, ole.openstream(fname).read()))))
stream = ole.openstream(fname).read()
> if options.select == ‘a’ \
> or (‘%s%d’ % (prefix, counter)) == options.select \
> or (options.select == ‘m’ and SearchAndDecompressSub(stream) != None) :
> StdoutWriteChunked(DumpFunction(DecompressFunction(DecodeFunction(decoders, options, stream))))
> if options.select != ‘a’ \
> and options.select != ‘m’:
Comment by Tamas — Thursday 16 April 2015 @ 23:38
[…] will warn you that it contains macros! To analyze them, let’s use Didier Stevens’s tool oledump to analyze the […]
Pingback by Hack in Paris Challenge Wrap-Up | /dev/random — Wednesday 29 April 2015 @ 20:23
Just a oledump typo I noticed. Towards the top it says “XML insize ZIP.” I think you meant “inside.”
Comment by Anonymous — Saturday 9 May 2015 @ 14:34
Thanks!
Comment by Didier Stevens — Sunday 10 May 2015 @ 20:12
I used your latest version oledump_V0_0_15.zip and using the similar command like emldump.py E8397CA1635.doc -s 3 -d | oledump.py -p plugin_http_heuristics.py. I am not getting the pastebinURL. But while executing i can able view the pastebin link through fiddler.Please help me.
Comment by Bharani — Wednesday 13 May 2015 @ 18:56
You also need to use the dridex plugin.
Comment by Didier Stevens — Wednesday 13 May 2015 @ 18:57
In this blog they never used the dridex plugin “http://bartblaze.blogspot.be/2015/05/new-malicious-office-docs-trick.html”.please suggest me where i have to provide dridex plugin in the command “emldump.py E8397CA1635.doc -s 3 -d | oledump.py -p plugin_http_heuristics.py”
Comment by Bharani — Wednesday 13 May 2015 @ 19:13
It’s simple, read the man: oledump.py -m emldump.py E8397CA1635.doc -s 3 -d | oledump.py -p plugin_http_heuristics,plugin_dridex
Comment by Didier Stevens — Wednesday 13 May 2015 @ 19:15
This one also not working.I have send you the malware sample in your gmail ID.
Comment by Bharani — Wednesday 13 May 2015 @ 19:28
Thank you so much for your updated version.It is working fine.Once again thanks.
Comment by Bharani — Thursday 14 May 2015 @ 11:51
Hello Didier,
Your scripts are wonderful. I am currently use oledump (with added exit codes) as external addon with my own antispam to filter (and quarantine) office documents which contain macros. Works like a charm.
Thanks
Comment by Philippe — Thursday 4 June 2015 @ 18:13
@Philippe Cool, that’s a good idea. Can you tell me more about the exit codes you use?
Comment by Didier Stevens — Thursday 4 June 2015 @ 18:19
Thank you for this very useful tool which was a great help today against “.doc” malware attacks
Jean-Côme
Comment by Anonymous — Tuesday 9 June 2015 @ 15:51
Hi Didier
Typically, if you run an enterprise mail server, as I do (for, let say an administration, sort of), you should quarantine each and every office document containing VBA. Exactly what I do, with your precious tool. I use sys.exit(exitcode) where exitcode is set when a document contains macro module.
Nowadays, those trojan loaders (2 or 3 stages) are very poorly detected by antiviruses. It is easy to remove and quarantine possibly dangerous documents (by their extensions), but you cannot refuse those office documents because they are part of our administrative work.
And this is where oledump.py play a very useful role. It comes as an addon of my (own-brewed) antispam, Spam-HL, which itself is called by my mail server (MDaemon).
I added a module that identifies the attachments both by their extensions and their signature, and process them accordingly. This way, even a .doc which would have been renamed in .docx would raise a “mitsmatch” and… a quarantine. I also make use of your PDF tool, even if it is not able to scan 100% of the documents. I just search for Javascript flags…
This way, 99,5% of the spam and 100% of the viruses are stopped before reaching my (so precious) users.
This is a must, since my server is well known and very exposed, I get almost all versions of zero-day trojans, each and every day… They would gently pass any antivirus solution, without problem (I have Kaspersky on the mail server, Clam on the firewall, and Avira on the Workstations : just a bunch of useless crap. The only thing the antiviruses are able to catch without failing, nowadays, is your money. Technically speaking they are worse than old dos-era antivirus like Thunderbyte or even MsAntivirus.
Anyway , this is the way I use your tools. Again, thank you for making them widely available.
Philippe
Comment by Philippe — Saturday 13 June 2015 @ 11:26
[…] is a new version of oledump with a couple of bugfixes and a new feature: […]
Pingback by Update: oledump.py Version 0.0.17 – ExitCode | Didier Stevens — Friday 26 June 2015 @ 9:44
[…] supposto potesse contenere un file exe nascoto o delle macro malevole, così abbiamo lanciato oledump per analizzare i vari settori del […]
Pingback by Analisi Documento Word con Macro Malevole - Shielder — Saturday 27 June 2015 @ 12:45
Dear Didier,
Thats great work, thanks for your effort. Heuristic HTTP analysis is very nice , however many macro enabled malwares, they mostly try to exploit the outlook MAPI function, where it has been used as a keylogger or document leaking tools. Have you ever worked on detecting such functions?
Regards,
Pascal
Comment by pascal — Monday 29 June 2015 @ 8:56
@pascal Do you have a sample? Can you share the MD5?
Comment by Didier Stevens — Monday 29 June 2015 @ 20:27
[…] AutomaticDestinations files are the OLE files, so you can analyze them with oledump. There are a couple of tools that can extract information from these […]
Pingback by Jump List Forensics | Didier Stevens — Monday 3 August 2015 @ 0:01
[…] oledump: Examine suspicious Microsoft Office files […]
Pingback by REMnux: Distribución de Linux especializada en en el análisis de malware | Skydeep — Thursday 20 August 2015 @ 1:49
[…] Demoing the new –cut option in my dump tools like oledump.py […]
Pingback by Cut Cut Cut … | Didier Stevens Videos — Tuesday 13 October 2015 @ 0:47
[…] further dig into these artifacts we will use another great tool. Oledump created by Didier Stevens. This tool allows you to analyze OLE files. As stated in the manual page: […]
Pingback by Malicious Office Document delivering Dyre | Count Upon Security — Tuesday 13 October 2015 @ 22:14
Hi , I try to use latest version oledump_V0_0_18.zip with python 3.5 and olefile-0.41but when I use C:\oledump>oledump.py File “C:\oledump\oledump.py”, line 710 exec open(plugin, ‘r’) in globals(), globals()
What’s wrong?
Comment by Fabrizio — Tuesday 27 October 2015 @ 15:31
Python 3 is the problem. Read this: https://blog.didierstevens.com/2015/07/20/if-you-have-a-problem-running-my-tools/
Comment by Didier Stevens — Tuesday 27 October 2015 @ 15:34
[…] oledump reveals VBA macros in the document, but the plugins are not able to extract a URL: […]
Pingback by Analysis Of An Office Maldoc With Encrypted Payload (Quick And Dirty) | Didier Stevens — Thursday 5 November 2015 @ 0:01
[…] is another tool for office document analysis (also to mention: didier stevens oledump) which also supports pre 2007 file formats. When applying it once for the word document it extracts […]
Pingback by Teaser on the Troopers16 Incident Analysis Workshop: Analyzing the current Spam Flood - Insinuator — Friday 18 December 2015 @ 11:56
[…] emldump is able to analyze the multipart MIME file, and detect the MSO file (part 3). oledump can analyze MSO […]
Pingback by MIME File With “Header” | Didier Stevens — Tuesday 22 December 2015 @ 0:00
[…] you can see a part of code used in that macros. Kasperksy extracted it using oledump tool written by Didier Stevens […]
Pingback by APT BlackEnergy. Cyber attacks in Ukraine. GREAT’s analisys. | Russian Hackers INFO — Saturday 30 January 2016 @ 2:46
[…] you can see a part of code used in that macros. Kasperksy extracted it using oledump tool written by Didier Stevens […]
Pingback by APT BlackEnergy. Cyber attacks in Ukraine. GREAT's analisys. ⋆ Russian Hackers INFO — Saturday 30 January 2016 @ 4:31
when I run python oledump.py “file.doc” I get an error File “oledump.py”, line 768
exec open(plugin, ‘r’) in globals(), globals()
Comment by Anonymous — Monday 1 February 2016 @ 20:17
Comment by Didier Stevens — Monday 1 February 2016 @ 20:25
[…] même étapes que pour Dridex. Pour la suite, nous allons extraire les macro du fichier office via oledump (le cousin belge du breton […]
Pingback by Locky l’épidémie | Cryptobourrin — Saturday 20 February 2016 @ 9:04
[…] are two good tools, that I know of, for looking at Microsoft Office files, Didier Stevens’ oledump; and Decalage’s oletools. Oletools contains the olevba.py script which will do some useful […]
Pingback by An Exercise in Deobfuscating MS Word Macros Using Linux | Malware Musings — Sunday 21 February 2016 @ 10:22
Hi,
I’m getting the following error with oledump 0.0.22 , Python 2.7, OleFileIO_PL-0.30 (although i’ve tried newer versions including the latest one), OS: Win 8.1 Pro x64
C:\oledump>oledump.py SCAN_Invoice.doc
Traceback (most recent call last):
File “C:\oledump\oledump.py”, line 1588, in
sys.exit(Main())
File “C:\oledump\oledump.py”, line 1585, in Main
return OLEDump(args[0], options)
File “C:\oledump\oledump.py”, line 1495, in OLEDump
oXML = xml.dom.minidom.parse(oStringIO)
File “C:\Python27\lib\xml\dom\minidom.py”, line 1918, in parse
return expatbuilder.parse(file)
File “C:\Python27\lib\xml\dom\expatbuilder.py”, line 928, in parse
result = builder.parseFile(file)
File “C:\Python27\lib\xml\dom\expatbuilder.py”, line 207, in parseFile
parser.Parse(buffer, 0)
xml.parsers.expat.ExpatError: syntax error: line 1, column 0
Comment by Anonymous — Sunday 28 February 2016 @ 12:17
That’s most likely because the file you are analyzing is not an OLE file, but a heavily obfuscated MIME type file. I’ve seen several these last days. You have to start the analysis with my emldump.py tool. What is the MD5 of your sample?
Comment by Didier Stevens — Sunday 28 February 2016 @ 14:40
Thanks for the quick reply.
The MD5 of the file is faf75220c0423f94658618c9169b3568 ; SHA1 ca60ed32b312417a6213d1db12c19c3682dc4622
Comment by Anonymous — Sunday 28 February 2016 @ 15:06
It’s indeed an obfuscated MIME type file. Here is the command to analyze it (extract the URL):
findstr /v AJ7ESAgBBEIGllvGiAgBhpiWAwIAnwaICAEAnsRICAEKCEg faf75220c0423f94658618c9169b3568.vir | emldump.py -s 6 -d | oledump.py -s 12 -d | re-search.py -n url
The findstr command will filter out the second line in the MIME type file that causes emldump.py to not recognize the MIME structure.
Comment by Didier Stevens — Sunday 28 February 2016 @ 15:28
It worked.
Two questions (this is my first shot at looking through malware-type documents in order to understand how they do what they do):
1. is there any way i could output the macros to a plain text file?
2. the string used as an argument for findstr – is it standard to all MIME type files?
Thanks a lot for the help and the awesome tools!
Comment by Anonymous — Sunday 28 February 2016 @ 16:11
1) yes, use option -s to select the stream(s) and -v to decompress the macros. Many of my Python tools (including oledump.py) come with a man page: use option -m or –man.
2) no, not at all, this second line in the file is not standard, it is included by the maldoc authors to confuse MIME type file parsers and decoders.
Comment by Didier Stevens — Sunday 28 February 2016 @ 16:22
Hi Didier! Great tools and great work!
Please help on this: https://www.virustotal.com/en/file/1b3d43d2d2a6d67858dd3867b976f2f3921417ad155c9f49bbbd5f269b0e2c48/analysis/
python ~/File_Analysis/emldump.py -H -s 6 -d INV00849\ -\ 66106986.doc_original | python ~/File_Analysis/oledump_V0_0_22/oledump.py -s 9 -v
We want to get the malicious URLs but we couldn’t yet.
Thank you in advance!
Comment by Anonymous — Monday 7 March 2016 @ 15:33
Try this:
emldump.py -f -s application/x-mso -d d6d14a38460a95ea17193dcc6720a02b.vir.zip | oledump.py -s 20
Comment by Didier Stevens — Monday 7 March 2016 @ 16:00
Thank you very much! Amazing and great tools!
Comment by Anonymous — Monday 7 March 2016 @ 17:00
[…] used oledump to extract the […]
Pingback by Infocaos | Locky Ransomware Arrives via Email Attachment — Wednesday 16 March 2016 @ 16:02
Hi Didier, thanks for your tools and effort on these. Trying emldump and oledump on this: https://www.virustotal.com/file/7755a176bb16d014aed21b0827734eb044c54aad1829396eb9a413729b4f0b4a/analysis/1458316211/ the macros look incomplete? I think there is supposed to be a download URL
Comment by Anonymous — Friday 18 March 2016 @ 18:40
No, it’s complete. But it contains a VBE file. Take a look at my last blogpost.
Comment by Didier Stevens — Wednesday 23 March 2016 @ 19:34
[…] scripting content inside the doc, it was not in easily-readable text format. Didier Stevens “oledump.py” came to the […]
Pingback by Writeup – WhereWouldWeBeWithout (Bsides Canberra 2016) | Advanced Persistent Jest — Friday 22 April 2016 @ 11:09
[…] zipdump can also be used to pipe a sample into my other analysis tools like oledump.py. […]
Pingback by Major Update For zipdump.py | Didier Stevens — Wednesday 1 June 2016 @ 0:00
Running into an issue with https://www.virustotal.com/en/file/e8dfe85021bdddb33bdb63ef7f6dab8f76baaf419f3332581bccefacf0d9213a/analysis/
I have version 0.42 of olefileio_pl installed and running version 0.0.24 of oledump.py. See error below;
A: word\vbaProject.bin
Traceback (most recent call last):
File “/tmp/bits/oledump/oledump.py”, line 1624, in
sys.exit(Main())
File “/tmp/bits/oledump/oledump.py”, line 1621, in Main
return OLEDump(args[0], options)
File “/tmp/bits/oledump/oledump.py”, line 1522, in OLEDump
ole = olefile.OleFileIO(cStringIO.StringIO(content))
File “/usr/lib/python2.7/site-packages/olefile/olefile.py”, line 1142, in __init__
self.open(filename, write_mode=write_mode)
File “/usr/lib/python2.7/site-packages/olefile/olefile.py”, line 1399, in open
self.loaddirectory(self.sectDirStart)#i32(header, 48))
File “/usr/lib/python2.7/site-packages/olefile/olefile.py”, line 1723, in loaddirectory
self.directory_fp = self._open(sect)
File “/usr/lib/python2.7/site-packages/olefile/olefile.py”, line 1796, in _open
if not self.ministream:
AttributeError: OleFileIO instance has no attribute ‘ministream’
Comment by Par Osterberg Medina — Tuesday 14 June 2016 @ 14:42
First and foremost… Thank you for this tool! I have one suggestion to make, based on a malicious document I received… I was really unable to decode the payload using the decoders provided with oledump.py, but had immediate success using the Windows Script Decoder that I found there; https://gist.github.com/bcse/1834878 It may be a decoder you’d like to take a look at. Thanks.
Comment by Denis Roy — Thursday 30 June 2016 @ 22:51
Answer to Osterberg Medina: this error happens with some malformed files. olefile has been improved since version 0.43 to handle them properly. You may update olefile easily using “pip install -U olefile”, or download the latest version from https://pypi.python.org/pypi/olefile/#downloads. Philippe.
Comment by decalage0 — Monday 11 July 2016 @ 20:50
[…] oledump will allow you to dump the various streams of the document, or if you’re in a tight analysis environment and speed is more important than thoroughness, you could just ‘ride-or-die’ and execute the macro. I have always thought DMX and Fetty were onto something, so let’s go for ‘ride-or-die’. […]
Pingback by WildFire Ransomware Catching On - OpenDNS Security Labs — Wednesday 13 July 2016 @ 17:31
I received a file this morning on my email client and after doing some research, I came across this tool. I was able to successfully view the stream with the macro, however I’m at a loss on how to decrypt it.
This is what comes up when I run oledump.py with the VBA summary plugin.
http://pastebin.com/yzdDCyrm
Comment by Rarona00 — Monday 8 August 2016 @ 18:58
What’s the md5 hash?
If you don’t know how to read code, you can’t decode it.
Comment by Didier Stevens — Monday 8 August 2016 @ 19:13
Dang, I was hoping one of your plugins would be able to do it automatically….the http heuristic plugin doesn’t pull up anything. I definitely don’t know how to read code. I was just curious what it was trying to download exactly.
Comment by rarona — Monday 8 August 2016 @ 19:26
This doesn’t look like a downloader, but a dropper. That’s why my plugins can’t help. If you give me the MD5 hash, I can take a look.
Comment by Didier Stevens — Monday 8 August 2016 @ 19:36
[…] So it is a simple Doc file (non xml). Let’s use olevba from Oletools and oledump […]
Pingback by Weaponized DOC with TeslaCrypt (?) « int3 (0xcc) — Saturday 3 September 2016 @ 10:10
[…] the first two steps identifying the streams the VBA macro was located and extracting the code with oledump-py by didier stevens. We found the embedded exe file ojGLBWnEuEy.exe is being run by the VBA […]
Pingback by Documents From Hell Part 2 | War and Code — Saturday 10 September 2016 @ 3:53
[…] extract stream information, including dates. The script appears to be complementary to Didier’s oledump. More […]
Pingback by Week 36 – 2016 – This Week In 4n6 — Sunday 11 September 2016 @ 12:10
Hi I’m having a problem eith using your tool oledump/ Is there any chance to analyze my file
Comment by mario — Wednesday 28 September 2016 @ 13:06
If it’s on VirusTotal then post the hash here.
Comment by Didier Stevens — Wednesday 28 September 2016 @ 13:08
[…] Preuve que les pirates se lassent peut-être : en tous les cas, la puissance olevba ou oledump peut s’exprimer pleinement pour en extraire rapidement des informations pertinentes à […]
Pingback by Anodin Odin | Cryptobourrin — Monday 3 October 2016 @ 12:28
[…] oledump.py and […]
Pingback by oledump xor kpa | Didier Stevens Videos — Friday 7 October 2016 @ 12:19
Hi Didier,
First let me say thanks for all your work! I was hoping you could provide some advice on a file i been looking at. I’m trying to extract the URL from the file using oledump.py and the http_heuristics plug in. When I ran it it provided me with an encoded output. I was wondering if there is another plugin i should use in conjunction to de-obfuscate the output. Here is the MD5 hash at VT below.
59f4198617a912bd7caaf7a36c76233c
Thank you!
Comment by HFW — Monday 10 October 2016 @ 21:55
[…] oledump.py, translate.py, […]
Pingback by Maldoc VBA: .pub File | Didier Stevens Videos — Tuesday 11 October 2016 @ 10:38
It’s too complex for the plugins, you have to decode it manually. Here is one way to do this: https://videos.didierstevens.com/2016/10/11/maldoc-vba-decoder-xls/
Comment by Didier Stevens — Tuesday 11 October 2016 @ 11:02
Thanks! I attempted to follow the instructions you provided in your video but it appears that this one (and its siblings) is proving to be uniquely different that does not want to spit out the ascii or unicode dump from the decoder.xls. Would you have any additional thoughts on a strategy to extract the shellcode?
Comment by HFW — Tuesday 11 October 2016 @ 15:08
I was able to extract the payload following the method I showed in the video. The payload is a command that drops and executes a VBS script via cmd.exe.
The encoded payload is in variable BlsNUgCJ in Sub TZOqN3O.
Comment by Didier Stevens — Tuesday 11 October 2016 @ 15:24
[…] oledump.py, […]
Pingback by Maldoc VBA: decoder.xls | Didier Stevens Videos — Friday 14 October 2016 @ 13:27
[…] oledump.py, […]
Pingback by Analyzing Office Maldocs With Decoder.xls | Didier Stevens — Friday 14 October 2016 @ 13:27
[…] oledump.py, […]
Pingback by Maldoc VBA: Decoding With Excel | Didier Stevens Videos — Monday 17 October 2016 @ 7:49
Hi Didier,
I spent the past couple days trying to re-trace your steps on how you extracted the payload but to no avail. What was the function that you used to track down the decoding? I didn’t want to run the entire sub in TZOqN3O since it included the GetObject call.
Comment by HFW — Tuesday 18 October 2016 @ 21:00
[…] The VBA macro code can be extracted with a free open-source tool: oledump.py. […]
Pingback by Malicious Document Targets Belgian Users | NVISO LABS – blog — Wednesday 16 November 2016 @ 6:59
I just downloaded oledump so i could examine a MS Word document and when I run oledump.py on Python 3.5 it returns a syntax error at this point “exec open(plugin, ‘r’) in globals(), globals()” at the end of the word “open”. I don’t know Python and don’t know what to do. I would like to examine the macros in a Word doc.
Comment by Craig Gallichotte — Tuesday 22 November 2016 @ 17:44
Please read this: https://blog.didierstevens.com/2015/07/20/if-you-have-a-problem-running-my-tools/
Comment by Didier Stevens — Tuesday 22 November 2016 @ 19:34
Thank you, Didier.
Comment by Craig — Tuesday 22 November 2016 @ 20:26
[…] a look with oledump.py at this sample (md5 b231884cf0e4f33d84912e7a452d3a10), we see it contains a large VBA macro […]
Pingback by Analyzing an Office Maldoc with a VBA Emulator | NVISO LABS – blog — Wednesday 7 December 2016 @ 14:01
[…] Tools: oledump.py […]
Pingback by Sleeping VBS Really Wants To Sleep | Didier Stevens Videos — Sunday 11 December 2016 @ 21:19
First, thank you for writing this.
I’m getting an error when I attempt to run oledump.py on Win8.1 x64 with Python 3.6.0 x64. The error, on line 787, is:
exec open(plugin, ‘r’) in globals(), globals()
^
SyntaxError: invalid syntax
I have decompressed all the files in the .zip archive to a directory and attempted to run the oledump.py script with a .doc file as an argument
python \oledump\oledump.py 30347.doc
Thanks,
Mark
Comment by Mark — Wednesday 11 January 2017 @ 20:55
Please read this: https://blog.didierstevens.com/2015/07/20/if-you-have-a-problem-running-my-tools/
Comment by Didier Stevens — Wednesday 11 January 2017 @ 20:57
[…] sample we received is a .docx file, with oledump.py we can confirm it doesn’t contain VBA […]
Pingback by Maldoc: It’s not all VBA these days | NVISO LABS – blog — Wednesday 8 February 2017 @ 9:04
[…] The next step is to examine any embedded scripts that may be in the document. To do so, we need to decode the document and extract the VBA Module Streams based on the MS-OVBA specification published by Microsoft. There are several good open source tools that are available to extract these streams (e.g., oledump written by Didier Stevens). […]
Pingback by Microsoft Office Malware Dropper targets Apple Mac OSX – Kevin Douglas — Sunday 19 February 2017 @ 20:00
I have a macro file inside another macro file. to the readout from oledump is
python oledump.oy -v bad.docx
A: Word/embeddings/oleObject4.bin
A1: Value
A2: ‘\x01Ole10Native’
A3: Value
B1: Value
B2: ‘\x01Ole10Native’
How might i read those Objects? None of them are marked as M for Macro.
Comment by Robert — Wednesday 1 March 2017 @ 0:29
This doesn’t look like normal output from oledump. Did you sanitize the output?
Comment by Didier Stevens — Wednesday 1 March 2017 @ 6:33
[…] oledump.py, re-search.py and […]
Pingback by Maldoc Deobfuscation: Character Removal | Didier Stevens Videos — Monday 6 March 2017 @ 9:05
[…] new version of oledump.py adds some extra features for YARA rule […]
Pingback by Update: oledump.py Version 0.0.27 | Didier Stevens — Tuesday 7 March 2017 @ 0:00
[…] using Oledump.py to analyze this Word document we get the following […]
Pingback by .LNK downloader and bitsadmin.exe in malicious Office document | NVISO LABS – blog — Friday 24 March 2017 @ 10:56
[…] Tools: oledump.py. […]
Pingback by Maldoc Deobfuscation: Plugin sub-str | Didier Stevens Videos — Monday 3 April 2017 @ 19:17
[…] Tools: oledump.py. […]
Pingback by oledump & YARA | Didier Stevens Videos — Monday 3 April 2017 @ 19:18
[…] Microsoft Office oledump oledump.py Examine suspicious Microsoft Office files remnux-didier (APT) https://blog.didierstevens.com/programs/oledump-py/ Examine Document Files: Microsoft Office oletools olevba, olebrowse, oletimes, rtfobj, pyxswf, etc. […]
Pingback by Remnux-A tool for reverse engineering Malware – Infohub — Saturday 8 April 2017 @ 22:40
[…] this is an ole file, we can analyze it with oledump.py: we dump the file with option -d and pipe it into […]
Pingback by Analysis of a CVE-2017-0199 Malicious RTF Document | NVISO LABS – blog — Wednesday 12 April 2017 @ 13:11
[…] tools (oletools and oledump) were used to initially examine this document. Oletools was used to provide the metadata associated […]
Pingback by Attackers Leverage Excel, PowerShell and DNS in Latest Non-Malware Attack – Trey's I.T. Security Blog — Monday 17 April 2017 @ 18:54
[…] I expect the embedded file to be a Word document with macros, I’m going to analyze it with oledump. So in stead of writing the embedded file to disk, I’m going to extract it to stdout (-d -) […]
Pingback by Malicious Documents: The Matryoshka Edition | Didier Stevens — Thursday 20 April 2017 @ 0:02
[…] Tools: rtfdump, oledump […]
Pingback by CVE-2017-0199 Demo | Didier Stevens Videos — Saturday 22 April 2017 @ 22:26
[…] Tools: rtfdump, oledump […]
Pingback by CVE-2017-0199 & Metasploit – Analysis | Didier Stevens Videos — Saturday 22 April 2017 @ 22:30
[…] pdf tools, oledump.py, […]
Pingback by Malicious Documents: The Matryoshka Edition | Didier Stevens Videos — Sunday 23 April 2017 @ 19:36
Hi Didier, thank you for sharing these tools. I’m using oledump(v0.0.27) and elmdump(v0.0.9) to analyze a .doc malware(SHA 256: f0bbe894f6e71690f80866b3c218f3330af8c0d5c6c6660963ace57fa6a1d592), but oledump says “is not a valid OLE file”, and elmdump finds only text plein. Could you give me some advice? How can I locate the malicious code?
Comment by WP — Wednesday 26 April 2017 @ 12:50
It’s not a .doc or MIME file, it’s a vbe file.
Comment by Didier Stevens — Thursday 4 May 2017 @ 7:11
Thanks a lot! I’ve decoded that.
Comment by WP — Thursday 4 May 2017 @ 15:19
[…] contents. So use binwalk, rename as zip or whatever. Inside we have a vba bin file. We can use oledump.py to view its […]
Pingback by S21SEC [DCS17CTF] – Finlandia – tunelko's blog — Wednesday 17 May 2017 @ 11:25
Didier, Is there a way to bruteforce a password protected docx using oledump? Today there are several samples coming out that I want to analyze but I can only get the sample. I’m guessing in the SPAM message with the malicious attachment it gives the recipient the password, but since I don’t have it (not being shared yet) I can’t see any of the streams. If you want to examine you can find the samples all appear in the same format as the one I’m trying to analyze: a10xc_71a_44yn29f_Paige Smith.docx
Comment by DB — Wednesday 12 July 2017 @ 18:20
No, you can not do that with oledump.
Comment by Didier Stevens — Wednesday 12 July 2017 @ 18:28
[…] was asked if oledump.py can “scan” multiple files: it can not, it can only analyze a single file at a […]
Pingback by oledump.py *.vir | Didier Stevens — Saturday 22 July 2017 @ 22:18
[…] oledump.py, zipdump.py, base64dump.py, […]
Pingback by Emotet Maldoc & ViperMonkey – Didier Stevens Videos — Thursday 10 August 2017 @ 20:03
[…] oledump.py, […]
Pingback by It’s Not An Invoice – Didier Stevens Videos — Monday 21 August 2017 @ 19:59
[…] oledump.py, zipdump.py, base64dump.py, pecheck.py, […]
Pingback by Metasploit’s msf.docm Analysis – Didier Stevens Videos — Monday 21 August 2017 @ 20:39
Thank you very much for the script. Small company where I work received quite profound phishing email, and a colleague of mine unfortunately opened it (and allowed editing…). Anyhow, here I am trying to figure out which URLs script uses to download malware, so I could maybe find some info about the malware self. According to oledump.py -M the file (possibly macro too?) is made on 20th of August 2017. I would be grateful if someone could check this script or give any useful advice:
oledump.py -s 8 -v Rech-03674886877.doc
https://pastebin.com/XkHVTbyf
oledump.py -s 9 -v Rech-03674886877.doc
https://pastebin.com/KzPcxLNK
oledump.py -p plugin_http_heuristics.py Rech-03674886877.doc
https://pastebin.com/5mxpK86e
Comment by Denis Sorn (@DenisS0rn) — Monday 21 August 2017 @ 22:51
Your sample is a variant of a sample I analyzed here: https://isc.sans.edu/forums/diary/Its+Not+An+Invoice/22738/
Comment by Didier Stevens — Monday 21 August 2017 @ 22:55
Thanks a lot for your help
Comment by Denis Sorn (@DenisS0rn) — Tuesday 22 August 2017 @ 23:56
[…] new version of oledump adds support to decode strings like UNICODE strings (-t), and can dump strings […]
Pingback by Update: oledump.py Version 0.0.29 | Didier Stevens — Monday 16 October 2017 @ 0:00
[…] we convert the hexadecimal encoding to binary (oledump), we can spot another interesting […]
Pingback by Decoy Microsoft Word document delivers malware through a RAT – Malware in the wild — Wednesday 18 October 2017 @ 6:51
[…] or new Open XML format. The extension should help but if not, the file command should do it. Use oledump.py or Decalage’s VBA Tools and/or OLE Tools to perform some reckon (e.g. find streams, […]
Pingback by (Not) All She Wrote (Part 2): Rigged Office Documents (Part 1) – Security Over Simplicity — Tuesday 24 October 2017 @ 15:57
[…] shared a sample with me detected by many anti-virus programs on VirusTotal but, according to oledump.py, without VBA […]
Pingback by Analyzing A Malicious Document Cleaned By Anti-Virus | Didier Stevens — Tuesday 31 October 2017 @ 0:00
[…] new version of oledump.py detects and analyses orphaned streams. More info on orphaned streams can be found in this […]
Pingback by Update: oledump.py Version 0.0.30 | Didier Stevens — Monday 6 November 2017 @ 0:00
[…] oledump (Extract Macros from Office Documents) […]
Pingback by Creating a Simple Free Malware Analysis Environment – NETWORK SECURITY & ETHICAL HACKING & IOT — Friday 10 November 2017 @ 13:47
[…] Basic (VB) Script, contained within a macro in the document. The Macro was extracted (using oledump) and inflated, which resulted in an approximately 1800 line VBScript. The script contains a […]
Pingback by Threat Analysis: Malicious Microsoft Word Documents Being Used in Targeted Attack Campaigns | Carbon Black — Tuesday 19 December 2017 @ 17:24
I have python 2.7.10 installed, i attempt to run the following “oledump.py ..\Document2.doc” and i get no output at all, no exception, nothing. i tried it on multiple documents both binary and zipped do you have an idea why?
Comment by sahar — Sunday 7 January 2018 @ 15:17
What happens when you run zipdump.py on document2.doc?
Comment by Didier Stevens — Sunday 7 January 2018 @ 15:59
I get an output and can successfully read it, here is output:
{
Index Filename Encrypted Timestamp
1 [Content_Types].xml 0 1980-01-01 00:00:00
2 _rels/.rels 0 1980-01-01 00:00:00
3 word/_rels/document.xml.rels 0 1980-01-01 00:00:00
4 word/document.xml 0 1980-01-01 00:00:00
5 word/theme/theme1.xml 0 1980-01-01 00:00:00
6 word/comments.xml 0 1980-01-01 00:00:00
7 word/media/image1.png 0 1980-01-01 00:00:00
8 word/settings.xml 0 1980-01-01 00:00:00
9 word/styles.xml 0 1980-01-01 00:00:00
10 docProps/app.xml 0 1980-01-01 00:00:00
11 docProps/core.xml 0 1980-01-01 00:00:00
12 word/_rels/numbering.xml.rels 0 1980-01-01 00:00:00
13 word/people.xml 0 1980-01-01 00:00:00
14 word/fontTable.xml 0 1980-01-01 00:00:00
15 word/commentsIds.xml 0 1980-01-01 00:00:00
16 word/commentsExtended.xml 0 1980-01-01 00:00:00
17 word/webSettings.xml 0 1980-01-01 00:00:00
18 word/numbering.xml 0 1980-01-01 00:00:00
}
Comment by sahar — Monday 8 January 2018 @ 8:08
This means that your .doc file is actually a .docx file. And since .docx files don’t contain macros, oledump has nothing to report.
Comment by Didier Stevens — Friday 12 January 2018 @ 22:56
[…] new version of oledump can output the content of all streams in JSON format, and has a new plugin for MSI files: […]
Pingback by Update: oledump.py Version 0.0.33 | Didier Stevens — Monday 19 February 2018 @ 0:02
[…] ideas. This week’s private maldoc training was no different: here’s a new version of oledump with changes inspired by this […]
Pingback by Update: oledump.py Version 0.0.34 | Didier Stevens — Sunday 6 May 2018 @ 17:05
[…] Support for YARA rules is identical to my other tools, like oledump. […]
Pingback by Update: base64dump.py Version 0.0.9 | Didier Stevens — Tuesday 8 May 2018 @ 0:00
[…] This is how an encrypted .docx file looks like, when analyzed with oledump: […]
Pingback by Encrypted OOXML Documents | Didier Stevens — Thursday 7 June 2018 @ 0:00
[…] oledump.py, re-research.py, sets.py and […]
Pingback by Maldoc with DOSfuscation – Didier Stevens Videos — Sunday 19 August 2018 @ 10:21
[…] oledump.py, re-research.py, sets.py and […]
Pingback by Dealing With Numeric Obfuscation – Didier Stevens Videos — Sunday 19 August 2018 @ 10:32
[…] Tools: oledump.py. […]
Pingback by Maldoc Analysis & Linux Tools – Didier Stevens Videos — Sunday 19 August 2018 @ 10:35
[…] Tools: oledump.py. […]
Pingback by oledump: plugin_msg – Didier Stevens Videos — Sunday 19 August 2018 @ 10:49
[…] oledump.py, re-research.py, sets.py and […]
Pingback by Maldoc with DOSfuscation: example 2 – Didier Stevens Videos — Sunday 9 September 2018 @ 20:12
Hello. I’m your follower since 2 years ago. I truly appreciate your time and effort when you create oledump. This tool is very helpful.
I had read your Yara rules of RTF files. I wrote a mess for you to tell you my discover about signature of CVE-2017-11882 and CVE-2018-0802 and maybe more, hope this could be useful.
I found that signature when I copied malware object from RTF infected CVE-2017-11828 file to clean RTF file. It only work when I’m click on this object, not load when open MSWord anymore. So I found that it will work if object had the “\objupdate” control.
I agree that Control words \Objupdate can be used in legitimate documents, but seem like MSWord doesn’t add this control word in MS documents anymore, so if documents have this control words, it’s added by attacker. You can inserts some objects to see that, esspecially with some objects which attacker uses to exploit MSWord CVE-2017-0199, CVE-2017-11882, CVE-2017-8570.
You could read more in
http://www.biblioscape.com/rtf15_spec.htm.
Hope this help. Tell me about your opinion.
Comment by Le Thanh Tung — Saturday 6 October 2018 @ 1:49
[…] This OLE file can be decompressed and extracted with option -e, but pay attention to use option -q (quiet) so that oledump will only report the output of the plugin, and nothing else. This can then be piped into a second instance of oledump: […]
Pingback by Analyzing PowerPoint Maldocs with oledump Plugin plugin_ppt | Didier Stevens — Thursday 25 October 2018 @ 0:00
Didier, Thank you for this tool. It saved me from a month of rework after a corrupted Excel file wouldn’t show any VBA code.
Comment by Profex — Tuesday 6 November 2018 @ 22:35
Hello sir,
i have received XML based word document file which has encrypted VBS macro scripts. i have try to analyzed this sample or file but i could not get success. i have try your scripts but its not work on this file. please guide me this file analysis.
Sha1 : 038FEEC5FC63B07C317A07EC078CF1325D694B62
Comment by Arjun — Tuesday 4 December 2018 @ 11:26
What command did you use?
Comment by Didier Stevens — Sunday 16 December 2018 @ 11:11
[…] Tools: oledump.py […]
Pingback by oledump: plugin_ppt – Didier Stevens Videos — Monday 31 December 2018 @ 17:21
[…] rtfdump.py, oledump.py, format-bytes.py, […]
Pingback by Dissecting a CVE-2017-11882 Exploit – Didier Stevens Videos — Monday 31 December 2018 @ 17:22
Hi, is it possible to extract the VBA reference information for a VBA stream? I believe the VBA somehow holds a GUID and or a filepath for each of the entries.
Comment by Andrew Lockhart — Wednesday 23 January 2019 @ 16:18
The information is in there, but I only parse it for information displayed with option -i. Maybe this is what you need. Take a look, and let me know what is missing.
Comment by Didier Stevens — Saturday 26 January 2019 @ 13:40
[…] Tools: msoffcrypto-crack.py, oledump.py […]
Pingback by msoffcrypto-crack – Didier Stevens Videos — Monday 28 January 2019 @ 0:05
[…] oledump.py […]
Pingback by oledump – My Technical Notes — Monday 28 January 2019 @ 5:42
[…] Tools: oledump.py […]
Pingback by Analyzing a Simple HTML Phishing Attachment – Didier Stevens Videos — Monday 18 February 2019 @ 0:08
[…] Spreadsheets with Excel 4.0 macros can be analyzed with oledump.py and plugin plugin_biff.py. […]
Pingback by Maldoc: Excel 4.0 Macro | Didier Stevens — Friday 15 March 2019 @ 0:00
[…] Tools: oledump.py […]
Pingback by Didier Stevens Videos — Friday 15 March 2019 @ 0:04
I believe the check and warning for when an OLE file is not found inside a ZIP was a recent addition? I am using a MAC and MS Word and MS Excel for MAC. I have tried the tool with these file and get the message: “Warning: no OLE file was found inside this ZIP”. Any suggestion what might the issue?
Comment by Adam — Monday 18 March 2019 @ 0:44
It’s normal if the file doesn’t contain macros.
Comment by Didier Stevens — Monday 18 March 2019 @ 7:56
[…] Tools: oledump.py […]
Pingback by Maldoc Analysis: Excel 4.0 Macro – Didier Stevens Videos — Sunday 31 March 2019 @ 22:25
LOVE this tool. it’s amazing. I’m using it in a bash script to comb through various types of files for the less tech savvy. Question: I can’t seem to dump the stream on a .msg attachment and get the file.
“oledump.py -s -d file.msg > /dir/to/file.jpg”
for example I need to ensure people that are using this can’t actually TOUCH the file just run it through the rest of the scanning program then it will auto-delete at the end.
Comment by Anonymous — Friday 19 April 2019 @ 18:45
You command is wrong, you need to give -s an index number.
Comment by Didier Stevens — Sunday 21 April 2019 @ 7:57
Hi Didier Stevans , getting below error , please help,
c:\Python27>python.exe c:\Python27\Scripts\oledump_V0_0_42\oledump.py -h
File “c:\Python27\Scripts\oledump_V0_0_42\oledump.py”, line 977
exec open(plugin, ‘r’) in globals(), globals()
^
SyntaxError: invalid syntax
Comment by Arun — Monday 8 July 2019 @ 8:37
Please read this: https://blog.didierstevens.com/2015/07/20/if-you-have-a-problem-running-my-tools/
Comment by Didier Stevens — Monday 8 July 2019 @ 18:36
Hi Didier Stevans,
i am using Python 2.7.16 to run the script oledump.py but getting error ,
C:\Python27>python.exe “C:\Python27\Scripts\oledump_V0_0_42\oledump.py” Book1.xlsx
Warning: no OLE file was found inside this ZIP container (OPC)
Comment by Arun — Tuesday 9 July 2019 @ 7:58
Thank you Didier Stevans,
its working now , problem was there was no Macro in the file and OLE Storage was empty [My observation].
Comment by Arun — Tuesday 9 July 2019 @ 10:34
[…] oledump.py, base64dump.py, […]
Pingback by Analyzing Compressed PowerShell Scripts – Didier Stevens Videos — Sunday 28 July 2019 @ 20:49
[…] Analyzing the document The analysis of this Excel file starts with open-source tool oledump.py: […]
Pingback by Malicious Spreadsheet Dropping a DLL – NVISO Labs — Wednesday 18 September 2019 @ 11:29
[…] The binary file format of Office documents (.doc, .xls) uses the Compound File Binary Format, what I like to refer as OLE files. These files can be analyzed with my tool oledump.py. […]
Pingback by Quickpost: ExifTool, OLE Files and FlashPix Files | Didier Stevens — Monday 21 October 2019 @ 0:00
My I add my thanks for this life saving product. I had 2 weeks of unsaved macros in a Normal.dotm. Found this yesterday. Recovered it all. Thank you Didier.
Comment by Julian Turner — Friday 22 November 2019 @ 7:24
[…] oledump.py, […]
Pingback by Analyzing .DWG Files With Embedded VBA Macros – Didier Stevens Videos — Wednesday 18 December 2019 @ 22:42
[…] Take for example oledump.py. […]
Pingback by YARA “Ad Hoc Rules” | Didier Stevens — Tuesday 31 December 2019 @ 14:42
[…] Tools: oledump.py. […]
Pingback by oledump: plugin_http_heuristics – Didier Stevens Videos — Monday 10 February 2020 @ 20:02
[…] Inside this ZIP container, file vbaProject.bin contains VBA code.It can be analyzed with a tool like oledump.py: […]
Pingback by Evidence of VBA Purging Found in Malicious Documents – NVISO Labs — Monday 24 February 2020 @ 23:27
[…] oledump.py, pecheck.py, […]
Pingback by YARA: Ad Hoc Rules – Didier Stevens Videos — Saturday 4 April 2020 @ 13:57
[…] code will execute, even when digital signatures are enforced.When analyzing this PoC document with oledump.py, we see the message box code:When analyzing this PoC document with pcodedmp, we see the calculator […]
Pingback by Tampering with Digitally Signed VBA Projects – NVISO Labs — Thursday 4 June 2020 @ 20:30
[…] dealing with malicious Excel spreadsheets or Word documents, you always want to use the Python Oledump tool created by Didier Stevens. Let’s first run the tool on the file MT301 SWIFT PREPAYMAENT […]
Pingback by Your Swift PrePaymaent Order is Actually CVE-2017-11882 – InfoSec Topics — Tuesday 14 July 2020 @ 20:05
[…] file and executes it by starting explorer.exe with the script as an argument (Figure 1). The tool oledump by Didier Stevens is also capable of extracting information from user forms as has been […]
Pingback by Qbot's Deliver Method | Malware Analysis Spotlight | VMRay — Wednesday 16 September 2020 @ 16:21
Hi Didier, I have a malicious .xls document that even the most recent (0.0.17) version of plugin_biff can’t parse. Would you be interested in taking a look?
Comment by Jacob Gajek — Thursday 1 October 2020 @ 20:28
Yes, if it’s on VT, you can just post the hash.
Comment by Didier Stevens — Thursday 1 October 2020 @ 20:29
Thank you! MD5 is 3d63be3293cfbc82b42e77573243a5d6. Password is 1234.
Comment by Jacob Gajek — Thursday 1 October 2020 @ 20:36
The Excel file is password protected. You need to decrypt it first, like this: msoffcrypto-crack.py -o – 3d63be3293cfbc82b42e77573243a5d6.vir | oledump.py -p plugin_biff
https://isc.sans.edu/forums/diary/Password+Protected+Malicious+Excel+Files/25990/
Comment by Didier Stevens — Saturday 3 October 2020 @ 10:46
Ah, thank you! I misinterpreted the –password switch in oledump. Sorry for the false alarm.
Comment by Jacob Gajek — Saturday 3 October 2020 @ 21:06
No worries. You’re welcome.
Comment by Didier Stevens — Saturday 3 October 2020 @ 21:09
[…] Tools: oledump.py […]
Pingback by oledump.py: plugin_msg_summary – Didier Stevens Videos — Sunday 11 October 2020 @ 21:54
HI i hope that someone can help me here. I want to use oledump to analyse macros of a word file for my project. I donwloaded and unzipped the files but it doesnt seemed to work. when i try to use it the terminal says: oledump: command not found. I am using Ubuntu 20.04.1 LTS and Python 3.8.5. I am new to this so any help is appreciated.
Comment by Anonymous — Wednesday 4 November 2020 @ 11:24
From your comment, I get that you have not used the command line before? Or at least scripts from the command line. I don’t have help for that on my blog. But look at some basic intro like this one: https://www.educative.io/edpresso/how-to-run-a-python-script-in-linux
Comment by Didier Stevens — Thursday 5 November 2020 @ 20:39
Thank you it works now
Comment by Anonymous — Thursday 5 November 2020 @ 20:49
Hi, I am using your tool for a school lab and am using it on and old Maldoc 7a618482be272bb1fcb4af69a3f649a3. When I run oledump.pf -p plugin_http_heuristics 7a618482be272bb1fcb4af69a3f649a3, I am not seeing the http url? am I doing something wrong?
Comment by Anonymous — Wednesday 11 November 2020 @ 22:05
It means either it contains no URL, either it it too obfuscated
Comment by Didier Stevens — Friday 13 November 2020 @ 18:40
[…] oledump.py, […]
Pingback by Analyzing FireEye Maldocs – Didier Stevens Videos — Sunday 20 December 2020 @ 11:33
[…] here. As we know it’s an OLE file, we can use OLE parsing tools, such as Didier Stevens oledump to extract out specific streams (it even has a specific MSG plugin). The downside of this is that […]
Pingback by Metaspike CTF – Week 2 – “As per my previous email” | ThinkDFIR — Monday 28 December 2020 @ 2:30
[…] strings.py, oledump.py, zipdump.py, re-search.py, rtfdump.py and shellcode emulator […]
Pingback by Doc & RTF Malicious Document – Didier Stevens Videos — Tuesday 26 January 2021 @ 23:42
Hey Didier – I was just reading through Xavier’s new diary on DDE inclusions, https://isc.sans.edu/forums/diary/Dynamic+Data+Exchange+DDE+is+Back+in+the+Wild/27116, and it occurred to me to wonder if there was an option on oledump to extract potentially malicious dde inclusions from Office docs? After looking, I don’t see anything explicit, though you could use the Yara plugin to run your rule from https://blog.nviso.eu/2017/10/11/detecting-dde-in-ms-office-documents/. This might be a useful feature, assuming I haven’t missed something somewhere.
Thanks!
John
Comment by johnmccash — Friday 19 February 2021 @ 11:48
Hi John – yes, you can use it, with a small modification to the rule. Will explain it in a diary entry.
Comment by Didier Stevens — Sunday 21 February 2021 @ 10:19
[…] oledump.py, […]
Pingback by oledump and YARA DDE Rules – Didier Stevens Videos — Sunday 21 February 2021 @ 22:19
Take a look here: https://isc.sans.edu/forums/diary/DDE+and+oledump/27122/
Comment by Didier Stevens — Monday 22 February 2021 @ 7:09
Hi,
Great Tool, I have tried to use it but for some reason it only works on some files:
I am using the below:
C:\Users\eldri\OneDrive\Desktop\oledump>python oledump.py -p plugin_vbaproject.py “C:\Users\eldri\OneDrive\Desktop\Book1.xlsm”
This is the output but with others I get the Hash’s?
1: 64 ‘\x06DataSpaces/DataSpaceInfo/StrongEncryptionDataSpace’
2: 112 ‘\x06DataSpaces/DataSpaceMap’
3: 200 ‘\x06DataSpaces/TransformInfo/StrongEncryptionTransform/\x06Primary’
4: 76 ‘\x06DataSpaces/Version’
5: 11560 ‘EncryptedPackage’
6: 1289 ‘EncryptionInfo’
Can you please see whether I am doing something wrong?
Thanks
OTH
Comment by OTH — Saturday 27 March 2021 @ 14:18
To what hash are you referring?
Comment by Didier Stevens — Saturday 27 March 2021 @ 14:20
This Hash:
Hashcat hash ( -a 3 -m 110 –hex-salt)
hashcat.exe -a 3 -m 110 –hex-salt -D 1 -o cracked.txt hash.txt –force
Comment by OTH — Saturday 27 March 2021 @ 15:03
Hi Sorry,
I have replied twice but it keeps not showing. The Hash is the Dynamic one for VBA password
Comment by OTH — Saturday 27 March 2021 @ 15:49
The document you show, is an encrypted Office document. The plugin you are using is not for those kind of documents, it’s for unencrypted documents with a VBA password.
Comment by Didier Stevens — Saturday 27 March 2021 @ 20:07
Hi!
I’m trying to analyze a .xls file (received from an exercise). However, I receive the error “Error: file.xls is not a file.”, what does this error mean?
Comment by Mike — Wednesday 2 June 2021 @ 8:48
It means that the argument you gave to oledump.py, is not a file. It is something else, it could be a directory for example.
Comment by Didier Stevens — Wednesday 2 June 2021 @ 8:58
Even though the output of “file” looks like the following:
“Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: 0xdf, Last Saved By: 0xdf, Name of Creating Application: Microsoft Excel, Create Time/Date: Mon Mar 23 14:19:10 2020, Last Saved Time/Date: Sat Apr 25 19:43:56 2020, Security: 0”
Comment by Mike — Wednesday 2 June 2021 @ 9:14
On what OS are you?
Comment by Didier Stevens — Wednesday 2 June 2021 @ 10:49
arch linux running 5.12.7-arch1-1
Comment by Mike — Wednesday 2 June 2021 @ 10:56
What happens when you do this :
cat file.xls > file.xls.copy
python3 oledump.py file.xls.copy
Comment by Didier Stevens — Wednesday 2 June 2021 @ 10:58
I receive the same error:
“Error: file.xls.copy is not a file.”
However, I tried cloning the repo and and use the tools that way, and it works.
I initially downloaded it from aur, so there might be some issues there [1].
Thanks anyway for your help.
[1] – https://aur.archlinux.org/packages/python-oletools/
Comment by Mike — Wednesday 2 June 2021 @ 11:03
python-oletools is not my software, it’s @decalage2’s software
I develop oledump.py, he does not.
I have no idea how you can get oledump.py on your system by installing python-oletools from aur … you should ask them.
Comment by Didier Stevens — Wednesday 2 June 2021 @ 11:07
my mistake, should’ve cloned your repo from the beginning, and not download some other wrong version 🙂
thanks
Comment by Mike — Wednesday 2 June 2021 @ 11:10
yw 🙂
Comment by Didier Stevens — Wednesday 2 June 2021 @ 11:18
[…] Tool: oledump.py […]
Pingback by oledump Cheat Sheet – Didier Stevens Videos — Sunday 20 June 2021 @ 15:05
Hi Didier, I was hoping if I could get some help.
I am reviewing this sample 4fb331e4e5c6094e731690371687b110 and am trying to extract an Excel 4 macro from here, but am hitting a wall.
Oledump is stating there isn’t an OLE file inside.
However, public sandbox analysis reveals small pieces of the macro and I got a little bit more information from chunks in a hidden sheet of the document.
Comment by JT — Thursday 24 June 2021 @ 14:15
If it’s an xlsm file with Excel 4 macros, you have to use zipdump and xmldump. I have some blog posts about this.
Comment by Didier Stevens — Thursday 24 June 2021 @ 16:10
[…] oledump.py, zipdump.py, xmldump.py, translate.py, […]
Pingback by Obfuscated Maldoc: Reversed BASE64 – Didier Stevens Videos — Tuesday 23 November 2021 @ 19:39
[…] oledump.py, […]
Pingback by YARA Rules for Office Maldocs – Didier Stevens Videos — Saturday 27 November 2021 @ 12:10
I wonder if anyone faced the same issue that the -p plugin_msg_summary has issued to parse the correct To recipients when those are broken in multiple lines.
e.g.
”
To: bob ,
alice
”
is parsed to ” To: bob , ”
I figured out its due to the line parsing logic in the plugin (line 69-74) of plugin_msg_summary.py but not smart enough to fix that … anyone 😀 ?
Comment by Anonymous — Tuesday 30 November 2021 @ 14:21
Thank you. This tool has allowed me to recover hours of work from a corrupted vbaproject.bin file.
Comment by Anonymous — Tuesday 15 February 2022 @ 15:55
Great!
Comment by Didier Stevens — Tuesday 15 February 2022 @ 23:59
[…] oledump.py, xorsearch, […]
Pingback by Quick & Dirty Shellcode Analysis – CVE-2017-11882 – Didier Stevens Videos — Wednesday 9 March 2022 @ 11:03
[…] Tools: oledump.py […]
Pingback by Maldoc: non-ASCII VBA Identifiers – Didier Stevens Videos — Sunday 24 July 2022 @ 9:50
[…] oledump.py, re-search.py, hex-to-bin.py, translate.py, xorsearch, […]
Pingback by VBA Maldoc & UTF7 (APT-C-35) – Didier Stevens Videos — Sunday 4 September 2022 @ 14:41