This section gives an overview of my shellcode. Most shellcode is completely coded by hand by me (I use the free nasm assembler), but some shellcode has also been generated with the help of a C-compiler. I worked out a method to generate WIN32 shellcode with a C-compiler. By using special constructs in C and avoiding incompatible constructs, the C-compiler will emit position-independent code for the C functions designed to be converted to shellcode. The shellcode is extracted from the compiled EXE-file when the program is run.
Not only is it easier and faster to code shellcode with C in stead of assembly language; this method makes it also possible to debug shellcode with Visual C++2008 Express’ integrated debugger. I’m currently writing a tutorial for this method.
The shellcodes presented here do not use hardcoded WIN32 API function addresses, they use the PEB method to dynamically lookup the addresses (code published in The Shellcoder’s Handbook, you can find it in the include file sc-api-functions.asm).
Note that shellcodes available for download here are not restricted in the byte-values they may use. Most of them will contain 0x00-bytes. If this is an issue, I’ll provide you with a couple of decoders I developed to exclude specific byte-values.
I wrote an article in Hakin9 magazine how to write shellcode with a C-compiler.
Download:
ShellCodeLibLoader_v0_0_1.zip (https)
MD5: F6D4779097A8A11C412BDD47B7B1C8AE
SHA256: 3294A4322926476562AF34A80B8155638EFEEF38E401E69D6DB9BBB652C3EB58
The DLL-loading shellcode I used in my cmd.xls spreadsheet was generated with my C-Compiler method. You can download Joachim’s code, converted to shellcode with this method, here:
Download:
ShellCodeMemoryModule_V0_0_0_1.zip (https)
MD5: CEABB3A8A9A4A507BA19C52EE2CC5DA9
SHA256: 284344C909E623B0406BB38A67F5A7A1AEE2473721244EED52CCEBB8846B0500
The shellcode is in file ShellCodeMemoryModule.exe.bin (it contains the shellcode with an appended DLL that displays a MessageBox).
Finally, after extensive testing of this shellcode, I disassembled it with ndisasm and optimized it for size (2297 bytes in stead of 2634 bytes). But this step is only necessary if you want assembly code for your shellcode. This assembly code will be released when I’m done tweaking it 😉
Per request, I release my assembly code I’ve used in my previous blogposts to display a message box when the injected shellcode gets executed. It’s nothing special, but it will save you some time when you need a similar program.
Assemble the code with nasm like this:
nasm -o sc-mba-hello.bin sc-mba-hello.asm
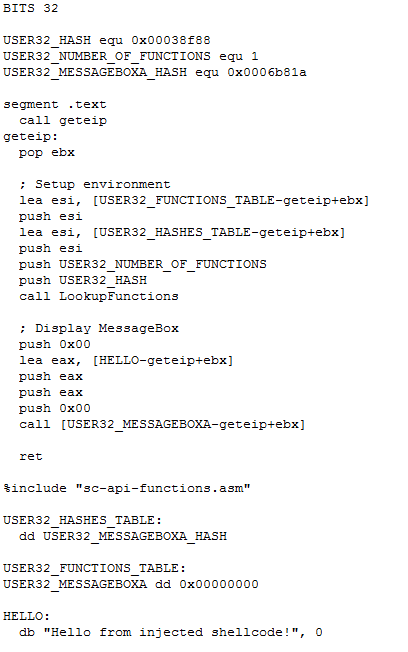
I use the DLL locating code published in The Shellcoder’s Handbook, you can find it in the include file sc-api-functions.asm. MessageBoxA is located in user32.dll, this dll has to be loaded in the process you’re injecting with sc-mba-hello.
sc-ods.asm is a similar program, calling OutputDebugStringA in stead of MessageBoxA.
The shellcode:
Another requested file (sc-winexec.asm) was added to my-shellcode_v0_0_3.zip: shellcode to launch calc.exe via a WinExec call. After that, the shellcode will exit with a call to ExitThread.
If you want this shellcode to launch another program than calc.exe, edit the last line of the assembly code to replace calc.exe with the desired program:
COMMAND: db "calc.exe", 0
2 other requested files (sc-ping.asm and sc-ping-computername-username.asm) were added to my-shellcode_v0_0_3.zip: shellcode to perform a ping. First one does a ping with a static payload, second one has dynamic payload (computername + username).
Shellcode to send a Twitter Update was added to my-shellcode_v0_0_4.zip. Before using/assembling the shellcode, you need to provide Twitter credentials and the text for the status update (url-encoded).
; Customize the following 3 TWITTER_ values according to your needs ; Notice that your Tweet has to be URL encoded! ; USER_AGENT is another value you might want to customize %define TWITTER_CREDENTIAL_NAME "user" %define TWITTER_CREDENTIAL_PASSWORD "password" %define TWITTER_TWEET_URL_ENCODED "This+is+a+Tweet+from+shellcode"
Shellcode to load a .NET assembly in the current process was added to my-shellcode_v0_0_5.zip. Before using/assembling the shellcode, you need to provide your own assembly, class, method and a parameter.
; Customize the following 4 DOTNET_ values according to your needs %define DOTNET_ASSEMBLY_VALUE "C:\HelloWorldClass.dll" %define DOTNET_CLASS_VALUE "DidierStevens.HelloWorld" %define DOTNET_METHOD_VALUE "HelloWorldMessageBox" %define DOTNET_ARGUMENT_VALUE "Call from shellcode sc-dotNET"
Example of a C# class:
using System;
using System.Windows.Forms;
namespace DidierStevens
{
public class HelloWorld
{
public static Int32 HelloWorldMessageBox(String message)
{
MessageBox.Show(message, "Hello World from .NET");
return 1;
}
}
}
x64 Shellcode
I’ve also started to write x64 shellcode, like this example.
Look for filenames starting with sc-x64 in the zip file (my-shellcode_v….zip).
Download:
my-shellcode_v0_0_8.zip (https)
MD5: 456F014F88A759B0A5CD15DC2C9F4BBD
SHA256: B924200D2F4674F9BC25AAB2C43397647E3F97AF27CBB394CBECCFBF2789D507
interresting thx mubix 😉
Comment by kermass — Sunday 14 February 2010 @ 14:11
Any chance you can write some shellcode to do a DNS lookup on a given domain?
Comment by Ron — Sunday 14 February 2010 @ 18:24
@Ron do you have an example of what you want to do, for example in C?
Comment by Didier Stevens — Sunday 14 February 2010 @ 18:53
Sure, I’m just thinking something like: gethostbyname(“xxx”)
The reason is, I have the authoritative server for my domain, so I’d use that for detecting a vulnerability (by looking up my own domain and seeing the request come).
Comment by Ron — Sunday 14 February 2010 @ 19:14
@Ron I’m not sure I understand why you need shellcode. You know that you can do this with nslookup, with a simple C program (or even in VBA).
So why do you want shellcode? Shellcode doesn’t usually interact with the user, and here, it would have to ask you for a hostname and a DNS server, and then display the results.
Comment by Didier Stevens — Sunday 14 February 2010 @ 19:54
I think I was writing that too soon after waking up. 🙂
My thought is this: I see a vulnerable service on a remote box (say, NTP). I want to verify that it’s vulnerable without worrying about it having an ingress/egress firewall. So, I throw some shellcode with a domain name hardcoded into it that simply does gethostbyname(“xxx”), and I watch my dns server to see if the request gets made.
Now that I think more, it’d probably be easier to just use an exec-style shellcode to run “ping xxx” instead of having special shellcode to do it.
Does that make sense?
Comment by Ron — Sunday 14 February 2010 @ 20:12
OK, now I understand. Yes, a ping would work to, but requires your shellcode to spawn a new process (the ping program).
You could just use that ubiquitous shellcode that downloads a file with URLDownloadToFileA and then executes it with WinExec.
You don’t need to execute the file, just download it from your website and monitor your logs. You can even use an empty file, but do host a file, otherwise, if you don’t host the file, URLDownloadToFileA will take long to execute (it will wait to timeout).
Comment by Didier Stevens — Sunday 14 February 2010 @ 20:46
The problem with URLDownloadToFileA, initially, is that it’ll typically be stopped by an egress firewall.
That being said, I think you’re on to something — I can use the URLDownloadToFileA shellcode with my domain as the URL, but return NXDOMAIN when it tries to download the code. The download will fail, and it’ll never attempt a HTTP connection anywhere, but I will be alerted that it attempted to do so.
Comment by Ron — Sunday 14 February 2010 @ 20:50
@Ron Yep, even with an egress firewall, it must perform a DNS lookup first, which you can catch. Unless the server has only access to an internal DNS that doesn’t forward queries to the outside world.
Comment by Didier Stevens — Sunday 14 February 2010 @ 20:55
[…] MemoryLoadLibrary: From C Program to Shellcode Filed under: Hacking, My Software, Shellcode — Didier Stevens @ 0:40 The DLL-loading shellcode I used in my cmd.xls spreadsheet was generated with a method I worked out to generate WIN32 shellcode with a C-compiler. You can find it on my new Shellcode page. […]
Pingback by MemoryLoadLibrary: From C Program to Shellcode « Didier Stevens — Tuesday 16 February 2010 @ 0:41
[…] Didier Stevens […]
Pingback by Exploit writing tutorial part 9 : Introduction to Win32 shellcoding | Peter Van Eeckhoutte's Blog — Thursday 25 February 2010 @ 16:24
[…] template can be found here. Leave a […]
Pingback by Writing WIN32 Shellcode With a C-compiler « Didier Stevens — Tuesday 4 May 2010 @ 10:17
[…] Didier Stevens […]
Pingback by [0x0027]Exploit writing tutorial part 9 : Introduction to Win32 shellcoding « Eohnik.c — Sunday 5 September 2010 @ 12:28
[…] This shellcode uses the library sc-api-functions.asm you can find in my shellcode repository. […]
Pingback by simple-shellcode-generator.py « Didier Stevens — Friday 23 September 2011 @ 9:04
[…] can get the code from my shellcode page. Look for filenames starting with sc-x64 in the zip file. Like this:LikeBe the first to like this […]
Pingback by x64 Windows Shellcode « Didier Stevens — Thursday 2 February 2012 @ 20:00
[…] can find this shellcode on my shellcode page. Like this:LikeBe the first to like this post. Leave a […]
Pingback by ExitProcess Shellcode « Didier Stevens — Monday 14 May 2012 @ 0:19
Does the MemoryModule shellcode provide a valid HINSTANCE on the entrypoint of the DLL?
Comment by Anonymous — Friday 13 May 2016 @ 6:31
No.
Comment by Didier Stevens — Friday 13 May 2016 @ 7:30
nice blog thank you!
Comment by Anonymous — Wednesday 18 May 2016 @ 5:14
It’s amusing to see my old comments here from 6 years ago, asking for help with something I can now do with my eyes closed. 🙂
Comment by Ron Bowes — Monday 23 May 2016 @ 17:28
Good for you!
Comment by Didier Stevens — Monday 23 May 2016 @ 18:39
[…] Tools: shellcode2vba.py, shellcode […]
Pingback by VBA Shellcode To Test EMET | Didier Stevens Videos — Sunday 27 November 2016 @ 8:45
how can create own shellcode to launch another program ? I want verry good explain from you. thank’s
Comment by invocker — Saturday 25 March 2017 @ 10:48
There’s an example in the zip.file.
Comment by Didier Stevens — Saturday 25 March 2017 @ 16:20