There are several how-tos on the Internet explaining you how to extract hashes from the Active Directory database file. I used this how-to for Kali Linux: https://blog.joelj.org/windows-password-audit-with-kali-linux/
The tools libesedb and ntdsxtract are used in this how-to.
I encountered an error when making libesedb:
libcfile_support.c:742:2: error: #error Missing file remove function
Make sure to read the comment from May 6, 2016 for this how-to: it offers a solution for this error. Edit libcfile/libcfile_support.c and add this line at the top:
#define HAVE_UNLINK 1
First we get the Active Directory database file I published and unzip it:
Next we use libesedb (command esedbexport) to export the tables from ntds.dit:
This may take some time, depending on the size of the database.
The exported tables are in folder ntds.dit.export:
Then we use ntdsxtract (command dsusers.py) to export the hashes (LM and NTLM) from the exported tables. First we export the hashes in a format suitable for John the Ripper. We store the files in folder dump. This command also takes the SYSTEM registry hive (file system) to extract the system key to decrypt the hashes.
We let the command create the folder dump:
Next the tool detects 2 schemas in the exported tables (objects 5 and 1480). First we try schema object 5:
This fails:
So we start again with schema object 1480, but first we need to remove the dump folder:
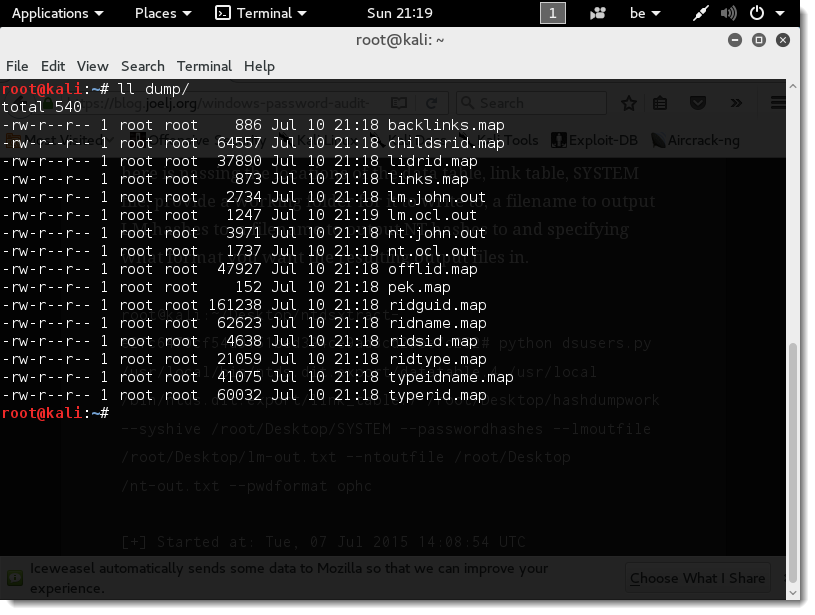
Now you can find the extracted hashes (lm.john.out and nt.john.out) in folder dump:
Next we repeat the same command but export hashes in a format suitable for hashcat:
Now you can find the extracted hashes (lm.ocl.out and nt.ocl.out) in folder dump:
If you want these hash files to crack the passwords without having to run through this how-to, you can download them here:
ntds-hashes.zip (https)
MD5: B0A84D756C211A97087BA307F0CE5739
SHA256: 009520798DD34831C47ADAC47D6DEB3C153FC44BD9D400A0BB813EBA46728D86
















[…] Now we will use hashcat and the rockyou wordlist to crack the passwords for the hashes we extracted in part 2. […]
Pingback by Practice ntds.dit File Part 3: Password Cracking With hashcat – Wordlist | Didier Stevens — Thursday 14 July 2016 @ 0:00
[…] cracking LM hashes we extracted from our Active Directory database file with a wordlist, we will perform a brute-force attack on the LM […]
Pingback by Practice ntds.dit File Part 4: Password Cracking With hashcat – Brute-force | Didier Stevens — Friday 15 July 2016 @ 0:01
[…] The next post provides a step-by-step guide for extracting hashes from the NTDS.DIT file; first in a format suitable for John the Ripper and then Hashcat. Practice ntds.dit File Part 2: Extracting Hashes […]
Pingback by Week 28 – 2016 – This Week In 4n6 — Sunday 17 July 2016 @ 12:51
[…] After password cracking examples with hashcat, I want to show you how to crack passwords with John the Ripper (remember we also produced hashes for John the Ripper: lm.john.out and nt.john.out). […]
Pingback by Practice ntds.dit File Part 6: Password Cracking With John the Ripper – Wordlist | Didier Stevens — Tuesday 19 July 2016 @ 0:01
[…] examiners how to crack passwords with a wordlist using John the Ripper and the hashes extracted in Part 2. Practice ntds.dit File Part 6: Password Cracking With John the Ripper – […]
Pingback by Week 29 – 2016 – This Week In 4n6 — Sunday 24 July 2016 @ 13:14
[…] Practice ntds.dit File Part 2: Extracting Hashes […]
Pingback by Practice ntds.dit File Overview | Didier Stevens — Monday 25 July 2016 @ 9:15
[…] In this video I show an alternative to my blogpost on extracting hashes from the Active Directory database file ntds.dit. […]
Pingback by Video: ntds.dit: Extract Hashes With secretsdump.py | Didier Stevens — Saturday 30 July 2016 @ 17:40
[…] Practice ntds.dit File Part 2: Extracting Hashes […]
Pingback by Overview of Content Published In July | Didier Stevens — Monday 1 August 2016 @ 0:00
[…] the LM and NTLM hashes with the hashes in this blogpost: they are the […]
Pingback by mimikatz: Golden Ticket + DCSync | Didier Stevens — Friday 12 August 2016 @ 8:04
[…] Practice ntds.dit File Part 2: Extracting Hashes […]
Pingback by Active Directory password audit using Kali | Stephen Dolphin — Wednesday 11 January 2017 @ 17:15
[…] extract password history from ntds.dit with ntdsxtract/dsusers.py, use option […]
Pingback by Practice ntds.dit File Part 9: Extracting Password History Hashes | Didier Stevens — Friday 3 March 2017 @ 0:00
[…] now to pull out some hashes. I followed Didier Stevens’ article to extract, and quickly did the first steps with esedbexport. But the extraction using […]
Pingback by Password cracking rig | securimancy — Saturday 3 June 2017 @ 17:51