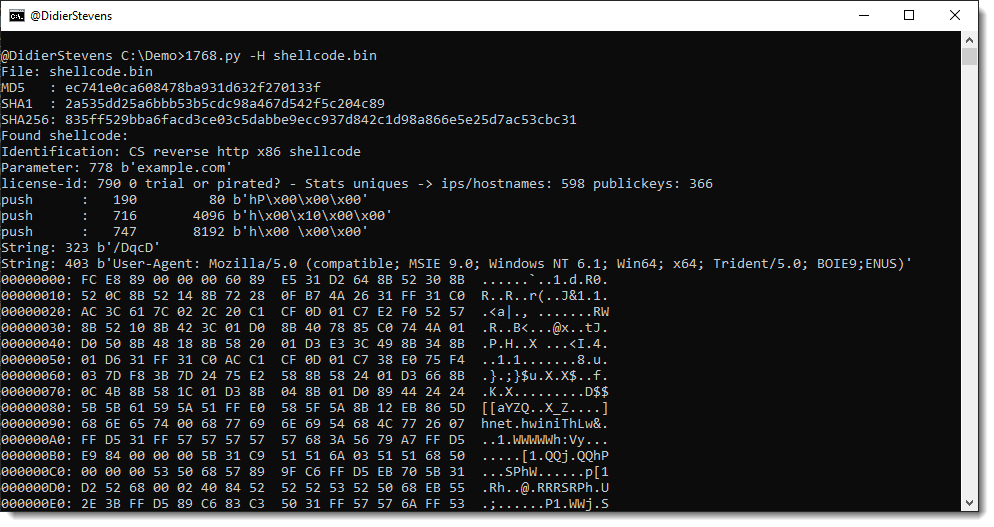
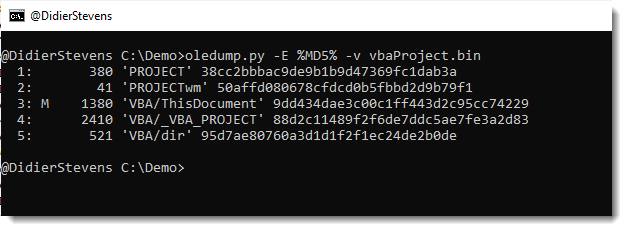
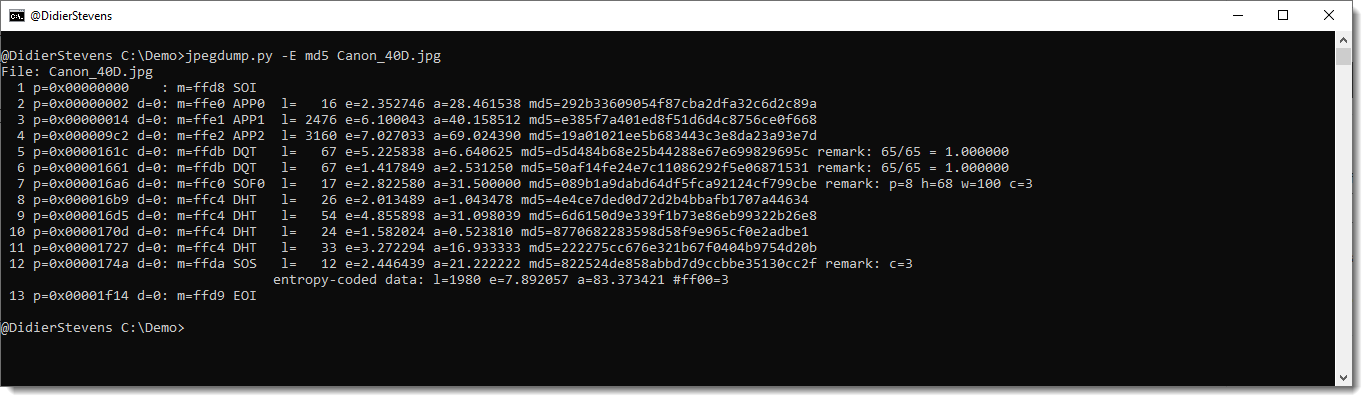
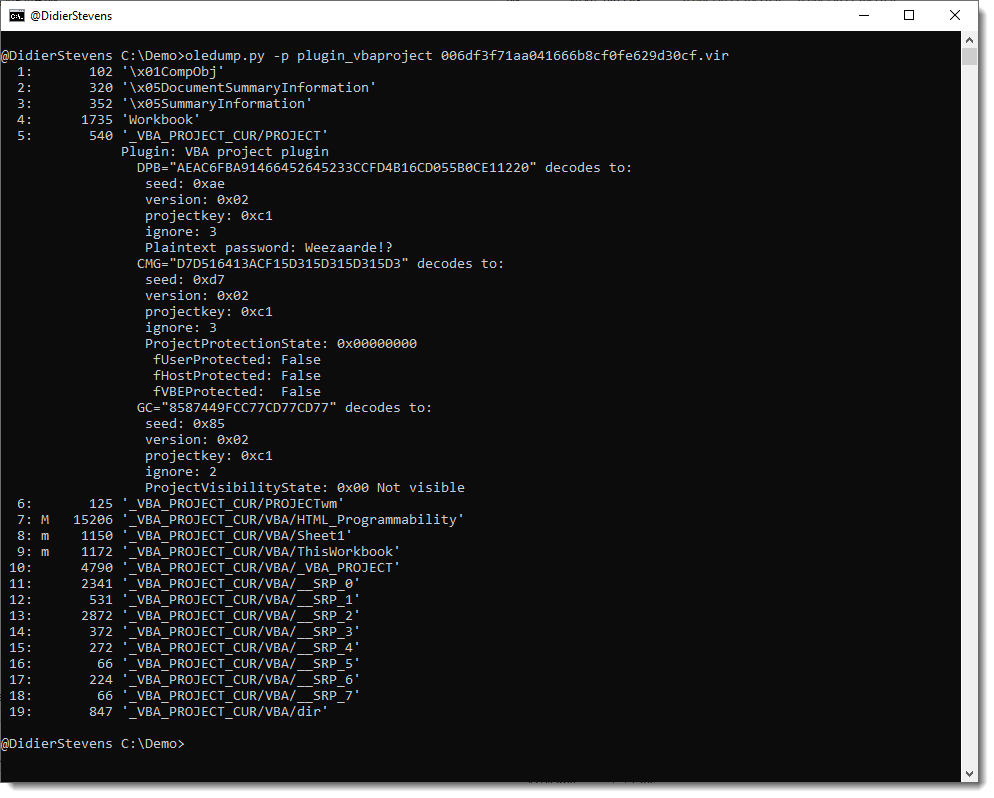
This new version of oledump.py brings some fixes and an update to plugin plugin_vbaproject to decode and display the password for plaintext passwords:


MD5: 20D89F0477ED7B533C2B0C6D27EC4255
SHA256: F67051EF2FA3FD42206C5ADFAC807C94ECD5F7F0F6427433B366217F675D3195