I updated oledump to handle a new type of malicious document: an XML file, not with VBA macros, but with an embedded OLE object that is a VBS file.
And the man page is finished. Run oledump.py -m to view the man page.
The sample I’m using here is 078409755.doc (B28EF236D901A96CFEFF9A70562C9155). The extension is .doc, but it is an XML file, not an OLE file.
First check:
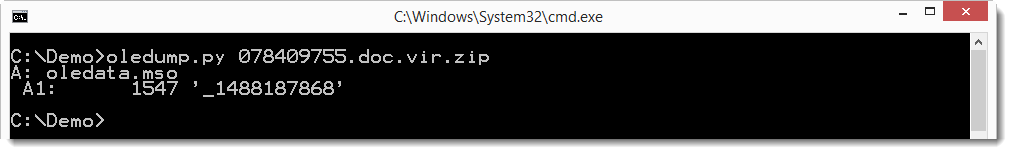
The XML file contains an OLE file with 1 stream.
Let’s take a look inside the stream:

Byte 0x78 could be the start of a ZLIB compressed data stream. Let’s checks this with option –decompress:

It is indeed ZLIB compressed, and the decompressed data seems to be another OLE file (D0 CF 11 E0).
So let’s pipe this decompressed OLE file into a second instance of oledump:

This OLE file contains an embedded object (Ole10Native). Let’s have a look:

It seems to be a .VBS file. Let’s have a look:

So this looks like VB Script with base64 strings. Let’s try to decode them with a plugin:

So now it’s clear what this maldoc does: launch PowerShell, download a file and store it as a .cab file in a temporary folder. Expand the downloaded .cab file to an .exe file, and then launch the .exe file. In other words, it is a downloader.
oledump_V0_0_13.zip (https)
MD5: 6651A674F4981D9AEDE000C1F5895B69
SHA256: 4452DF48F7D852140B4CD662AD95C6BC695F5F04009B37A367EB392384935C51