I read something very interesting in “Windows via C/C++” today: starting with Windows Vista, CreateProcess can start a program where you specify the parent process! This is something forensic investigators must be aware of when they analyse processes running on a Windows machine.
Normally the parent process of a new process is the process that created the new process (via CreateProcess). But when using STARTUPINFOEX with the right LPPROC_THREAD_ATTRIBUTE_LIST to create a process, you can arbitrarely specify the parent process, provided you have the rights (i.e. it’s your process or you have debug rights).
I developed a small tool to start a program while specifying its parent process: SelectMyParent. Here I use it to start notepad as a child of lsass.exe:
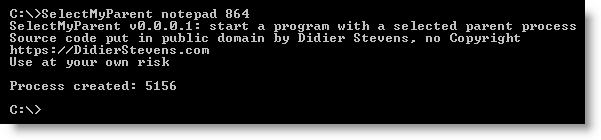
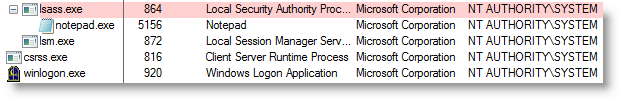
2 remarks about this example:
- to make lsass.exe a parent process, you need to use SelectMyParent with admin rights and elevate its rights (Run as administrator)
- the notepad process takes over the parent process’ account: NT AUTHORITY\SYSTEM
I don’t know how one can detect that a process’ parent is not the process that created it, because a process has no access to its extended startup info (only to its startup info). And it is the extended startup info that contains the attribute list with the handle to the parent process.
SelectMyParent version 0.0.0.1 is available here.
I’d like to expand on my questions that I asked via Twitter. Those being:
1. Are you able to move a currently running process under another one?
2. Are there any privileges applied to the parent/child relationship of processes?
You said that a child access the “inheritable handles”. I don’t know what exactly ‘handles’ are, but if you were able to migrate a running process under one that you created you might get some interesting permissions to it. Or say, Process A has handles H that Process B uses, if you were some how to hijack Process B or put yourself in between process A and process B, you might be able to alter the state of those handles.
But getting back to the ability of your app, for software that starts an “update” process, there might be some inheritable handles that you could get a hold of by impersonating the update process that it starts since most coders wont think about the security of child processes… yet.
Just thinking out loud.
Sweet program! 😉
Comment by mubix — Sunday 22 November 2009 @ 21:27
A handle is a pointer to a pointer to a kernel object.
And I too believe that this feature merits further investigation ;-). That’s why I posted my program so soon, so that others can play with it too.
FYI: my tool will not allow the new process to inherit handles. If you want this, change the code like this:
CreateProcess(NULL, argv[1], NULL, NULL, FALSE, …
->
CreateProcess(NULL, argv[1], NULL, NULL, TRUE, …
Comment by Didier Stevens — Sunday 22 November 2009 @ 21:49
[…] process is. This creates a problem. Read Didier’s post to find out what that problem is. Quickpost: SelectMyParent or Playing With the Windows Process Tree << Didier Stevens Tags: ( windows […]
Pingback by Interesting Information Security Bits for 11/23/2009 | Infosec Ramblings — Monday 23 November 2009 @ 23:04
Cool 🙂
I’ve ported the tool to Python and included it in my WinAppDbg debugger: http://sourceforge.net/apps/trac/winappdbg/browser/trunk/tools/SelectMyParent.py
This trick could also be used to thwart an antidebugging trick, as some packers check if their parent is explorer.exe or not.
Comment by Mario Vilas — Wednesday 25 November 2009 @ 0:57
This has always been the case on NT, actually. The underlying system call has always allowed you to specify an inherit from process handle (provided you have PROCESS_CREATE_PROCESS access to said processs — a sensitive access level).
It just so happens that the Win32 wrapper typically always uses the creator’s process handle as the inherit from process handle.
The link between a creator process and a ‘child’ process has always been extremely tenuous in NT.
Comment by Skywing — Thursday 3 December 2009 @ 19:11
@Skywing
Interesting. So the NtCreateProcess* functions exported by ntdll.dll have always allowed this, but it’s only starting with Vista that CreateProcess exported from kernel32.dll also allows this?
Comment by Didier Stevens — Thursday 3 December 2009 @ 19:22
Yes, that’s correct. Someone could have just as easily thunked down to the raw system call however and bypassed CreateProcess, so this is something that has required handling from the get-go and not just on Vista or later. It’s entirely possible to do exactly the same thing on earlier systems, and
Note that there is no security implication here as privileged access (PROCESS_CREATE_PROCESS) to a process is required to inherit from it. This access right is typically only given to the object owner, system, and administrators.
Comment by Skywing — Thursday 3 December 2009 @ 21:45
@Skywing Thanks for the clarification. And I agree there is no security issue.
Comment by Didier Stevens — Thursday 3 December 2009 @ 21:50
[…] Years ago I released a tool to create a Windows process with selected parent process: SelectMyParent. […]
Pingback by That Is Not My Child Process! | Didier Stevens — Monday 20 March 2017 @ 0:00
[…] powershell.exe, and other processes with an alternate parent. This feature takes advantage of an API, introduced with Windows Vista, to enable consent.exe to launch elevated processes with the […]
Pingback by Cobalt Strike 3.8 – Who’s Your Daddy? | Strategic Cyber LLC — Tuesday 23 May 2017 @ 13:57
[…] ago I wrote a C program to create a new process with a chosen parent process: selectmyparent. And recently I showed what process monitor and system monitor report when you use this […]
Pingback by Select Parent Process from VBA | Didier Stevens — Monday 10 July 2017 @ 0:00
Has anyone attempted to implement this in C#? Is this possible?
Comment by Craig — Monday 10 July 2017 @ 14:33
[…] Processes; similar examples of this were brought up in the DFIR community by Didier Stevens about 10 years ago TAU Threat Intelligence Notification: PPID Spoofing – Explorer […]
Pingback by Week 5 – 2019 – This Week In 4n6 — Sunday 3 February 2019 @ 8:50
[…] ago (as early as 2009), my colleague Didier Stevens wrote a blog post about parent process ID spoofing. Back then, most companies were not as secure as they are now, […]
Pingback by The return of the spoof part 1: Parent process ID spoofing – NVISO Labs — Friday 31 January 2020 @ 12:00