I wasn’t going to mention SAFER to restrict the rights of an application, because Software Restriction Policies can be bypassed. But a Tweet by Edi Strosar made me review my viewpoint. In this particular case, bypassing SRP is a non-issue, because the user is already local admin!
Software Restriction Policies allow you to force specific applications to run with a restricted token. As Michael explained it with AD GPOs, I’ll show it with local policies.
Enable SAFER policies for SRPs by adding DWORD registry key Levels (value 0x31000) to HKLM\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers:

Start the Local Security Policy administration tool and go to the Software Restriction Policies. You’ll have to create new policies if this is the first time you configure SRPs.

Create a new rule in Additional Rules. We’ll identify the application to restrict by its path and name, so create a Path Rule:

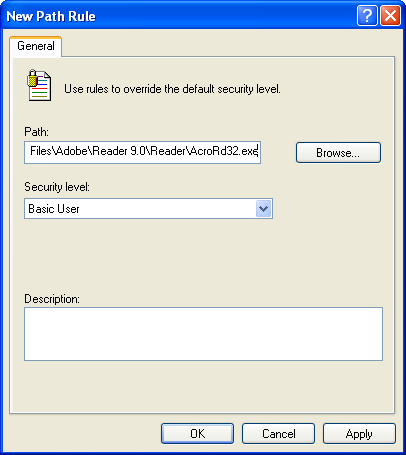
For the security level, select Basic User:

If you have no Basic User option, you forgot to update the registry before launching the administration tool:

Select the application to restrict:
This rule will force Adobe Reader to run with a restricted token:

Writing to SYSTEM32 is denied:

why not run using psexec utility from sysinternals like, “psexec.exe -l -d “
Comment by karthik — Monday 28 September 2009 @ 21:24
@karthik
We want to restrict the token of the process which ever way the application is launched. For malicious documents, the “reader application” can be started in many different ways:
1) Double-clicking the document in Windows Explorer.
2) Opening the document in your browser
3) opening the document in your e-mail client
…
For every of these cases, you want the application to run with restricted rights. So psexec is a solution, if you can configure your system to execute psexec for all of these different cases.
That’s why I talked about StripMyRights and the Image Execution registry entry. Because that’s one of the methods to make sure StripMyRights will proxy your application. Have you tested psexec with the Image Execution method? If it supports it, you can use it in stead of StripMyRights.
SAFER offers the advantage that you don’t need a proxy application to start the vulnerable application, and that it can be deployed with AD.
Comment by Didier Stevens — Monday 28 September 2009 @ 21:36
I see your point, agreed that AD GPO’s is much elegant solution. I generally launch (just configure short cuts once) my email client, browser, IM client (basically all that connect to internet) with stripped down privileges, so all their child processes also gets privileges stripped.
and I dont like windows explorer, its crappy and heavy. i use blackbox shell instead. 😉
your posts are very helpful, i enjoy reading it. thanks.
Comment by karthik — Monday 28 September 2009 @ 23:53
Didier,
Safer and StripMyRights.exe have differing terminology for their respective token levels. Can you tell me if the table below is correct, in terms of equivalent meanings?
Comment by Drewfus — Wednesday 5 May 2010 @ 0:30
@Drewfus Yes, these are equivalent
Comment by Didier Stevens — Wednesday 5 May 2010 @ 10:44
Thanks Didier.
Comment by Drewfus — Wednesday 5 May 2010 @ 12:49
Does SAFER prevent restricted applications from writing to \system32 only, or is there anything else that is restricted behind the scenes? Is it possible to extend protection to \windows directory as well?
Comment by dlimanov — Monday 14 June 2010 @ 17:27
@dlimanov SAFER makes the programs run with a restricted token, one of the implications of this restricted token is that you’re not a member of the local administrators anymore. This denies you the right to write to system32 (and other ACL-protected directories as well, like Windows).
Comment by Didier Stevens — Sunday 20 June 2010 @ 18:52