You’ve probably encountered malicious PowerShell scripts with an encrypted payload (shellcode, PowerShellScript, …).
Here is an example that I created:
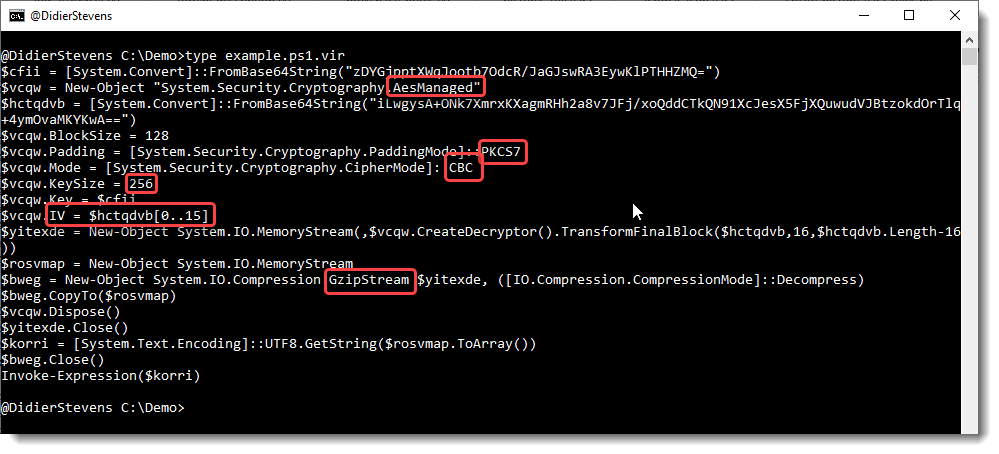
Update: this example is on pastebin: https://pastebin.com/QUGiWTHj
There are 2 BASE64 strings in this script. The first one (cfr. variable $cfii) is the encryption key. The second one (cfr. variable $hctqdvb) is the payload.
The script uses AES encryption, with a 256-bit key, CBC mode, PKCS7 padding and an initialization vector (IV) that is stored in the first 16 bytes of the payload (0..15).
And after the payload is decrypted, it has to be decompressed with the Gzip algorithm.
With base64dump.py, I can find the 2 BASE64 strings in the PowerShell script:

I select the second BASE64 string (payload) to pipe into translate.py, using the following small Python script (decrypt.py) to do the decryption:
from Crypto.Cipher import AES
from Crypto.Util import Padding
def Decrypt(data):
iv = data[0:16]
ciphertext = data[16:]
key = binascii.a2b_base64(keybase64)
oAES = AES.new(key, AES.MODE_CBC, iv)
return Padding.unpad(oAES.decrypt(ciphertext), 16)
This small script uses crypto functions from pycryptodome.
I use translate.py in fullread mode (-f –fullread, to “translate” the file in a single step, in stead of byte per byte) and use function Decrypt to decrypt the block of data, like this:
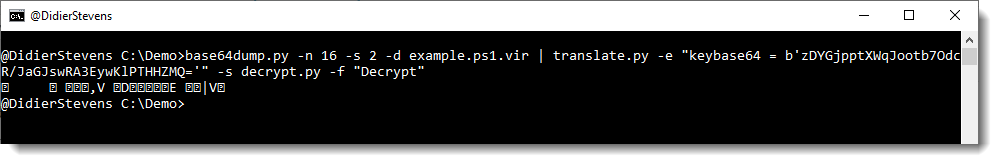
I load the script decrypt.py with option -s, and I pass the key as a BASE64 string via option -e.
The output is non-printable bytes, because the decrypted payload is Gzip compressed. I use translate.py again to do the decompression:
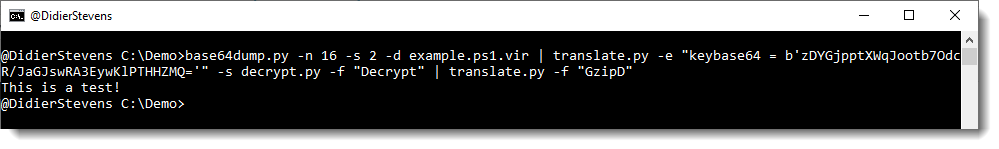
And now the “payload” I used is decrypted and decompressed: “This is a test!”













