This is something I’ve wanted to do for some time: take a command interpreter and transform it from an EXE into a DLL.
Why you ask? Well, because it’s a fun challenge 😉
But also because a DLL is loaded into a process. In a restricted environment, it can be injected into a legitimate process and thus bypass the restriction mechanisms.
Metasploit’s Meterpreter is another example of a command interpreter in DLL form.
cmd.exe from Microsoft is closed source, but there is an open-source variant available from the ReactOS project.
Compiling cmd.exe from ReactOS is simple: download the source-code and the ReactOS build environment. Install it, start the build environment and issue command make cmd. That’s all you need to do to compile cmd.exe (I used version 0.3.11).
Transforming the source code to generate a DLL in stead of an EXE is simple. You need to change 3 files.
Edit file cmd.rbuild and make these changes to the module element:
<module name="cmd" type="win32dll" installbase="system32" installname="cmd.dll" unicode="yes" crt="msvcrt">
Because I want to use this DLL in GUI-processes without console, I need to create a console. Edit file cmd.c and add AllocConsole(); to function cmd_main:
SetFileApisToOEM();
InputCodePage= 0;
OutputCodePage = 0;
AllocConsole();
hConsole = CreateFile(_T("CONOUT$"), GENERIC_READ|GENERIC_WRITE,
FILE_SHARE_READ|FILE_SHARE_WRITE, NULL,
OPEN_EXISTING, 0, NULL);
And because a DLL has another entry-function than an EXE, edit file main.c and replace function main with function DllMain:
#include <precomp.h>
INT WINAPI
DllMain(
IN PVOID hInstanceDll,
IN ULONG dwReason,
IN PVOID reserved)
{
switch (dwReason)
{
case DLL_PROCESS_ATTACH:
cmd_main(0, NULL);
break;
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
That’s it. Recompile with make cmd to generate cmd.dll
There are still some improvements we can make, but that’s for a later version: error messages are not displayed, exiting the shell terminates the host process, …
You can download the modified source files and compiled cmd.dll here.
This is a screenshot of cmd.dll injected inside Excel with my memory module shellcode:
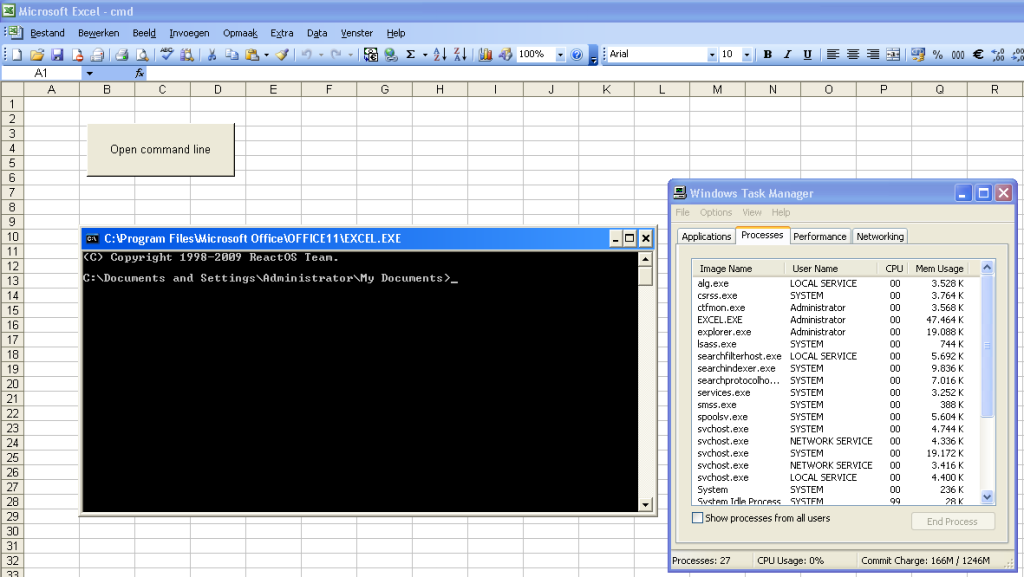
This could actually be very useful.
Can you with some VBA script run program in the “Excel-command-promt”?
Comment by Rickard — Thursday 4 February 2010 @ 8:38
@Rickard: if I understand your question, you want to run a VBA macro in Excel that sends commands to the “Excel-command-prompt”?
The only way I can think of is to use sendkeys and send keystrokes it to the “Excel-command-prompt” window.
Comment by Didier Stevens — Thursday 4 February 2010 @ 9:32
Hi,
Actually, when i want to inject a DLL and spawn a shell i use this code : http://support.microsoft.com/kb/105305
Hope i will be usefull 🙂
Cheers
Ivan
Comment by Ivan — Thursday 4 February 2010 @ 18:59
@Ivan: Merci! BTW, I think you would also need to do something to select the correct win station/desktop when you inject this in a service (no interaction with user desktop).
Comment by Didier Stevens — Thursday 4 February 2010 @ 23:41
[…] cmd.dll – didierstevens.com Take a command interpreter and transform it from an EXE into a DLL. […]
Pingback by Week 5 in Review | Infosec Events — Monday 8 February 2010 @ 14:28
[…] modified source code from ReactOS to transform cmd.exe into cmd.dll and regedit into a […]
Pingback by Excel with cmd.dll & regedit.dll « Didier Stevens — Monday 8 February 2010 @ 21:18
Thks, that made me experiment more with the ReactOS cmd.exe
version You can make the dll smaller by removing the string tables
languages (has no use there) and not using unicode (saves you macro
space) My cmd.dll is now 120 KB and the cmd.exe which uses the dll
is 64 KB (contains 1 string table) Its a perfect replacement for
the old MS version, no incompatibilities discovered yet.
Comment by Hans — Monday 3 January 2011 @ 15:21
Excellent!. I arrived here by Googling for “CMD.exe souce code” ;-).
I´ve been trying to find a cmd.exe replacement to use on my WinXP SP3 VMs because I often have a dozen open cmd windows inside the VM and need to know which is which, so I thought I´d recompile cmd.exe to update the wndows´ titlebar with the current path.
Before I do that, though, I wonder if perhaps there isn´t a COMSPEC parameter or other standard windows way to achieve this?.
Thanks!
FC
Comment by fcassia — Thursday 17 November 2011 @ 22:52
@fcassia there are some tools around that let you change the title of a Window.
And there are some commercial cmd replacements that offer multiple windows.
Comment by Didier Stevens — Friday 18 November 2011 @ 17:34
Excellent !!! Are there any problem with Windows server 2008 and Office 64 bits?
First, onto ‘Declare function’ we have to put ‘PtrSafe’, and … Do we have to modify shellcode cmd and cmd.dll?
Waiting for an answer
Regards !!
Comment by Ivan — Sunday 13 January 2013 @ 17:18
@Ivan This only works on Excel 32 bit. For it to work on 64-bit, cmd.dll needs to be compiled with a 64-bit compiler, the shellcode needs to be translated to 64-bit and VBA script needs to be translated to 64-bit.
If you are interested in 64-bit, I’ve a workshop: http://didierstevenslabs.com/products/x64-workshop.html
Comment by Didier Stevens — Sunday 13 January 2013 @ 18:11
[…] I took advantage of the rundll32.exe command to launch cmd.exe for me. This can be used for any DLL, but I was limited to system DLLs remaining on the box, and so far was unable to upload in anything like Didier Steven’s cmd.dll (https://blog.didierstevens.com/2010/02/04/cmd-dll/). […]
Pingback by Welcome | computer security and system designs — Saturday 31 January 2015 @ 23:42
[…] https://blog.didierstevens.com/2010/02/04/cmd-dll/ […]
Pingback by Bypass Windows AppLocker-IT大道 — Monday 18 January 2016 @ 3:06
[…] 参考资料: https://blog.didierstevens.com/2010/02/04/cmd-dll/ […]
Pingback by Bypass Windows AppLocker | z7y Blog — Tuesday 19 January 2016 @ 13:29
[…] References PowerShell without PowerShell – http://www.blackhillsinfosec.com/?p=5257 App Whitelisting Bypass – http://subt0x10.blogspot.com/2016/04/bypass-application-whitelisting-script.html Open Source Windows-like OS – https://www.reactos.org/ Open Source Windows-like OS – https://en.wikipedia.org/wiki/ReactOS How to convert EXE to DLL – https://blog.didierstevens.com/2010/02/04/cmd-dll/ […]
Pingback by Red + Blue = Purple – Black Hills Information Security — Wednesday 26 October 2016 @ 16:01
[…] Didier Steven’s has produced a nice write up on taking a third party command interpreter and converting it from .exe to .dll, for more information see: Didier’s Blog […]
Pingback by rundll32 lockdown – NyaMeeEain — Wednesday 11 April 2018 @ 9:13