Today I want to explain how I deal with a piece of malware that obfuscates its strings.
After dealing with the packing, we end up with an unpacked PE file. BinText reveals some strings, but not URLs. Searching for HTTP with XORSearch (version 1.1) doesn’t reveal any XOR encoding.
So let’s take a look with IDA Pro:

This is interesting! The strings are somehow obfuscated. Let’s go to this .data segment:

OK, so in this segment, all strings are obfuscated. This malware must have a routine to deobfuscate these strings before they get passed to functions like RegOpenKey…
Now let’s take a look at the code that references the start of this .data segment.
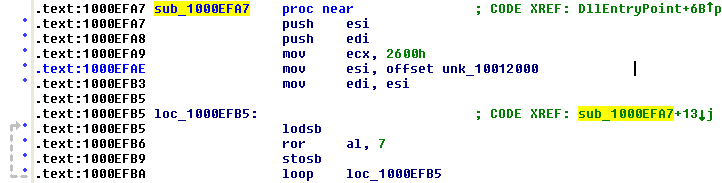
See the LOOP and the ROR instructions? They form a very good candidate for our deobfuscation routine. The loop goes through each byte of the .data segment (0x2600 is the size of the .data segment), and performs a ROR 7 on it.
We want to decode the strings, but unfortunately, the free XVI32 binary editor doesn’t support rotate operations, only shift operations. So we will use the 010 Editor, another binary editor (not free). This editor also supports binary templates. Let’s take a look at our malware file with the PE2 binary template. We select the .data segment like this:

And then we rotate all bytes in this segment 7 bits to the right:
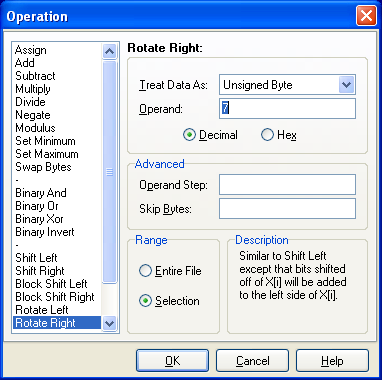
Bingo:

Let’s save this deobfuscated piece of malware and analyze it with IDA Pro:

Now the reversing becomes more easy, because we can read the strings.
This obfuscated malware prompted me to update my XORSearch tool and to write a Python script to manipulate bits.