This new version adds YARA support.
myjson-filter_V0_0_5.zip (http)MD5: CA8EAB44E283C2BFE0674CCDA1EE35EE
SHA256: A1E133E5BBB0F129156058E0E8DBD3834A23CEC6173BAFF0ADB79E46BDF48AAB
This new version adds YARA support.
myjson-filter_V0_0_5.zip (http)This new version adds two new values for option -l.
One could already use option -l P to locate all PE files inside an arbitrary binary file.
Option -l PE also adds entries for the extra (E) data, e.g., the data in between found PE files.
Option -l PO is like PE, but adds some more information for the other (O) files: the magic header (hex & ASCII).
pecheck-v0_7_16.zip (http)This is just a small update to my XOR known-plaintext attack tool, with some improvements on the algorithm.
xor-kpa_V0_0_8.zip (http)This updates changes the THP_READALL logic, and adds THP_ECHO_THIS and THP_ALLOW_LIST.
simple_listener_v0_1_3.zip (http)This new versions adds 2 new features:
Option -H adds a human hash for each hash:
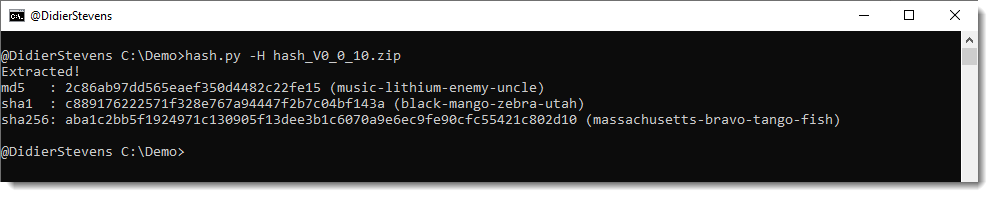
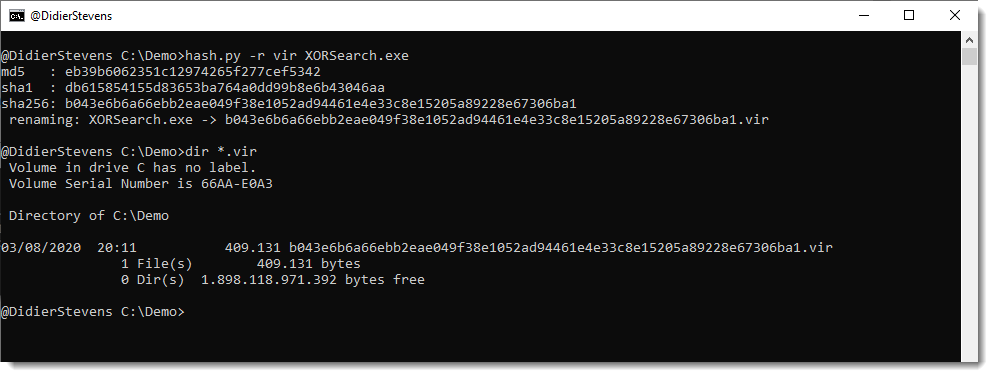
Option -r renames a file to its hash (hash) or to its hash with extension .vir (vir).
When more that one hash algorithm is used (default: md5, sha1, sha256), the last hash algorithm is used for the rename operation.
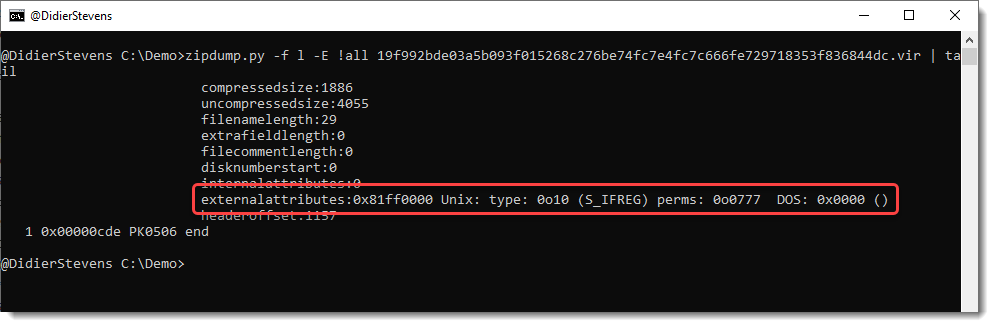
This update of zipdump.py adds parsing for external attributes and DOSDATE and DOSTIME fields when options -f and -E are used.

This update is just a definition update to detect MSO (ActiveMime files).
file-magic_V0_0_7.zip (http)This new update can produce JSON output for each part (option–jsonoutput).
emldump_V0_0_13.zip (http)This is an update linked to option -f l to find PKZIP records.
When option -E all is used, field externalattributes is parsed now: