This update to pngdump.py adds an index for chunks, and allows for the selection of a chunk via its index.
Monday 9 June 2025
Tuesday 3 June 2025
Update: search-for-compression.py Version 0.0.4
This tool is still beta.
VBA compression is now supported, besides zlib compression. Option -t (–type) was added so that one can choose the compression type to search for. Possible values are zlib (default) or vba.
And shortcut #p# was added to the yara option, to predefine these rules:
rule attribute_vb_name {
strings:
$a = "Attribute VB_Name = "
condition:
$a
}
rule dir {
strings:
$a = { 01 00 04 }
condition:
$a at 0
}I’ll explain in another blog post how these features can be used to analyze MS Access databases with VBA project.
Sunday 25 September 2022
Taking A Look At PNG Files with pngdump.py Beta Version 0.0.3
Here’s a new beta version of my tool pngdump.py, a tool to analyze PNG files.
I took a look at all files on MalwareBazaar with a PNG tag, and made updates to pngdump.py to handle them.
I found 3 types of “PNG” files.
First, files spoofing PNG files: files that are not PNG files, but have a .png extension.
Like .exe and .rar files:
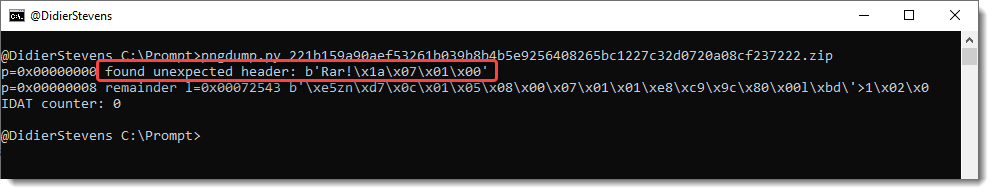

Second, valid PNG files with an appended payload:
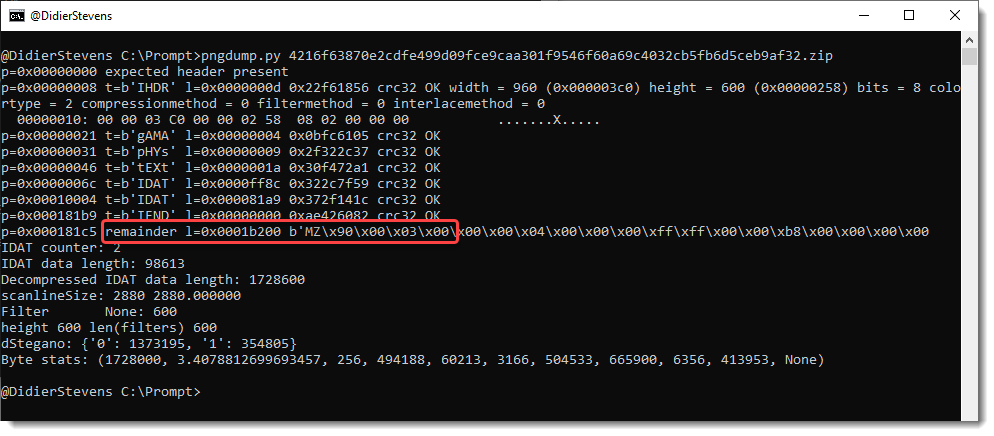

Third, invalid PNG files. For example, PNG files with the right record structure, but where the Zlib compressed image is replaced by an RC4 encrypted payload (IcedID):

I also have other samples, but that’s for another blog post.
Beta version 0.0.3 is available on GitHub.
Monday 21 February 2022
Beta: smtp-honeypot.py
This Python script is essentially a wrapper for the smtpd Python module.
I use it to receive emails, and write them to disk.
Sometimes I use this to exfiltrate (malicious) emails.
Sunday 16 July 2017
Beta: format-bytes.py
I needed a tool that can interpret bytes as various integers, so I came up with format-bytes.py:
I’m not happy yet with the layout of the output, that’s why it’s beta.
Wednesday 28 September 2016
decoder-search.py Beta
I’ve been developing a new Python program similar to XORSearch. decoder-search.py does brute-forcing and searching of a file like XORSearch, but it stead of simple operations like XOR, ROL, …, it can handle more complex translations. Templates for these translations have to be provided in a configuration file, for example like this:
expression ((byte + %i1:1-10%) ^ %i2:1-32%) % 0x100
This template specifies a translation expression that adds a number to each byte in the file, and then XORs the sum. The first integer added to each byte is brute-forced from 1 to 10 (%i1:1-10%), and the second integer used for the XOR operation is brute-forced from 1 to 32 (%i2:1-32%). Such an encoding has been used in the last hancitor maldoc samples.
Here is the result on a sample that contains an encoded EXE:
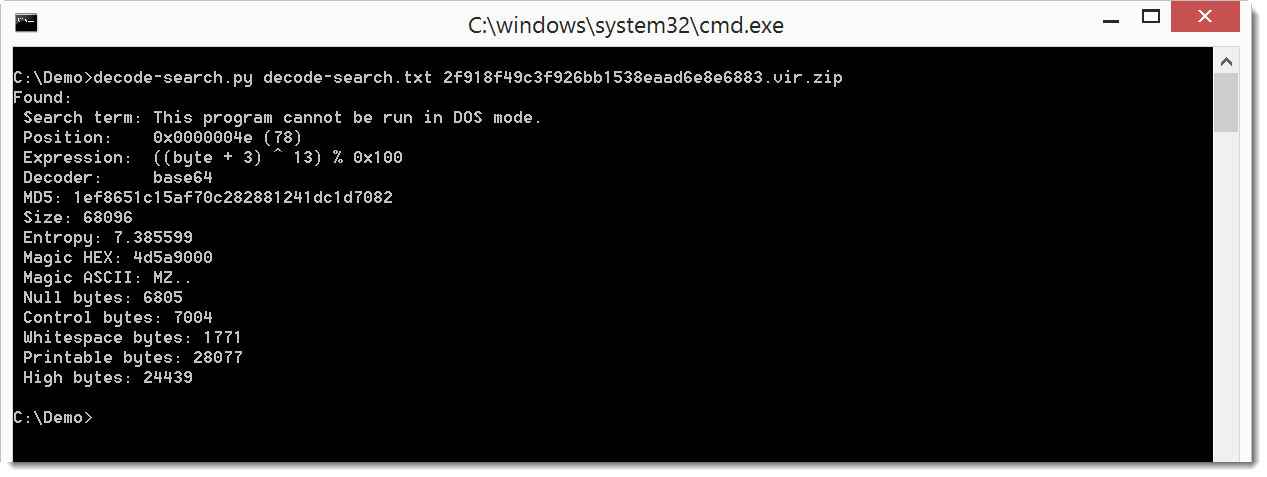
And here is the result on a sample that contains encoded URLs:
For me this tool is still in beta phase, because I might change the format of the configuration file in later versions, without providing backwards compatibility. You can find it in my GitHub Beta repository.

