XORSearch
XORSearch is a program to search for a given string in an XOR, ROL, ROT or SHIFT encoded binary file. An XOR encoded binary file is a file where some (or all) bytes have been XORed with a constant value (the key). A ROL (or ROR) encoded file has its bytes rotated by a certain number of bits (the key). A ROT encoded file has its alphabetic characters (A-Z and a-z) rotated by a certain number of positions. A SHIFT encoded file has its bytes shifted left by a certain number of bits (the key): all bits of the first byte shift left, the MSB of the second byte becomes the LSB of the first byte, all bits of the second byte shift left, … XOR and ROL/ROR encoding is used by malware programmers to obfuscate strings like URLs.
XORSearch will try all XOR keys (0 to 255), ROL keys (1 to 7), ROT keys (1 to 25) and SHIFT keys (1 to 7) when searching. I programmed XORSearch to include key 0, because this allows to search in an unencoded binary file (X XOR 0 equals X).
If you think the file is encoded with a 32-bit XOR key, use option k. Normally, XORSearch does a bruteforce attack with 8-bit keys and smaller. A 32-bit key bruteforce attack would take too long. Option -k instructs XORSearch to do a 32-bit dictionary attack in stead of a 8-bit bruteforce attack. The dictionary is extracted from the file itself: it is assumed that the 32-bit key is inside the file as a sequence of 4 consecutive bytes (MSB and LSB are both tried). Key 0x00000000 is excluded.
If the search string is found, XORSearch will print it until the 0 (byte zero) is encountered or until 50 characters have been printed, which ever comes first. 50 is the default value, it can be changed with option -l. Unprintable characters are replaced by a dot.
Usage: XORSearch [-siuhkpwWLxrS] [-l length] [-n [-+]length] [-f search-file] [-e byte] [-d encodings] file [string|hex|rule] XORSearch V1.11.3, search for a XOR, ROL, ROT, SHIFT or ADD encoded string in a file Use filename - to read from stdin Use -x when the file to search is a hexdump Use -s to save the XOR, ROL, ROT, SHIFT or ADD encoded file containing the string Use -l length to limit the number of printed characters (50 by default, 38 with option -p) Use -i to ignore the case when searching Use -u to search for Unicode strings (limited support) Use -r to reverse the file before searching Use -f to provide a file with search strings Use -n [-+]length to print neighbouring characters (before & after the found keyword) Use -h to search for hex strings Use -k to decode with embedded keys Use -S to print all strings Use -p to search for PE-files Use -w to search with wildcards Use -W to search with embedded wildcards Use -L to list embedded wildcards Use -e to exclude a particular byte-value from encoding Use -d to disable encoding(s) 1: XOR 2: ROL 3: ROT 4: SHIFT 5: ADD Options -l and -n are mutually exclusive Options -u and -h are mutually exclusive Options -k and -e are mutually exclusive Option -p is not compatible with options -i, -u, -h, -n and -r When using -p, do not provide a search string or use -f When using -W, do not provide a search string or use -f Use option -L without arguments or other options Source code put in the public domain by Didier Stevens, no Copyright Use at your own risk https://DidierStevens.com
Compiled with Windows gcc, Linux gcc and Xcode gcc.
Download:
Thanks to Google, I can no longer host this program on my own site. More info: FalsePositive GitHub Repository.
XORSearch_V1_11_4.zip
MD5: E66290D1EB15D9394C8D1264A09ECFE6
SHA256: BF20A1D76AAD83FC3AABEDC6DDC7F96B655DC94BEC3FA276A50AF6046EBB554C
XORStrings
XORStrings is best described as the combination of my XORSearch tool and the well-known strings command.
XORStrings will search for strings in the (binary) file you provide it, using the same encodings as XORSearch (XOR, ROL, ROT and SHIFT). For every encoding/key, XORStrings will search for strings and report the number of strings found, the average string length and the maximum string length. The report is sorted by the number of strings found, but can also be sorted by the maximum string length (use option -m). By default, the string terminator is 0x00, but you can provide your own with option -t, like the space character (0x20) in this example:
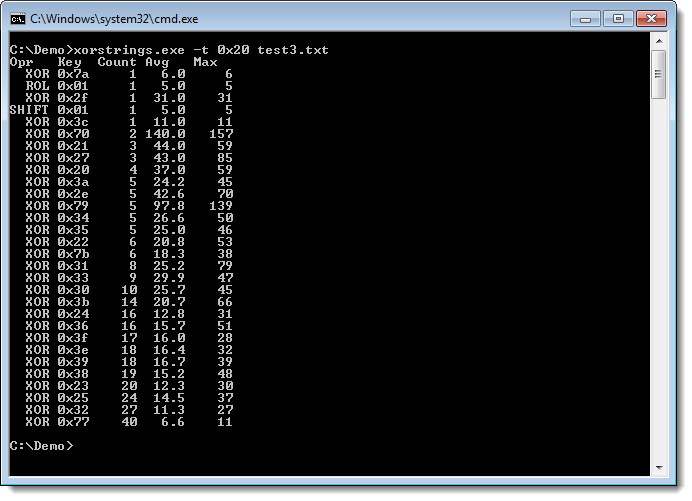
The output can also be formatted as a CSV file: use option -c to achieve this.
To dump the longest string found with each encoding and key, use option -d.
To view all strings with a particular encoding and key, use options -o and -k, like this:
xorstrings -o XOR -k 0x20 sample.exe
And to save the decoded files, use option -s. Files will be saved with an extension indicating the encoding and the key.
Usage: XORStrings [options] file XORStrings V0.0.1, look for XOR, ROL or SHIFT encoded strings in a file Use -s to save the XOR, ROL or SHIFT encoded file Use -d to dump the longest string Use -m sort by maximum string length Use -l to set the minimum string length (default 5) Use -t to set the string terminator character, accepts integer or hex number (de fault 0) Use -c to output CSV Use -o to select the operation (XOR, ROL or SHIFT) to perform (to be used togeth er with -k) Use -k to select the key for the operation to perform (to be used together with -o) Source code put in the public domain by Didier Stevens, no Copyright Use at your own risk https://DidierStevens.com
Compiled with Borland’s free C++ 5.5 compiler, Linux gcc and Xcode gcc.
XORStrings_V0_0_1.zip (https)
MD5: 27DA0B3BC5296179CB58181BDFF99F8D
SHA256: 5EA7E063A41E38E9E6277F1CD73FCEA2AEF50C33C44D75C226900314FF84A1B5
[…] XORSearch V1.1.0 Filed under: My Software — Didier Stevens @ 8:49 I’ve updated XORSearch: […]
Pingback by XORSearch V1.1.0 « Didier Stevens — Tuesday 30 January 2007 @ 8:49
thank you, comes in handy
Comment by mario — Tuesday 22 May 2007 @ 1:56
[…] prompted me to update my XORSearch tool to deal with ROL encoding. Feeling lazy, I only coded ROL support, not ROR. Or did I, what do […]
Pingback by XORSearch V1.2.0: XOR & ROL « Didier Stevens — Tuesday 14 August 2007 @ 6:34
[…] descifrando binarios XORSearch es una herramienta para buscar una cadena cualquiera de texto en un archivo binario, cuyos bytes […]
Pingback by XORSearch, descifrando binarios « TIDDER — Tuesday 21 August 2007 @ 10:40
[…] up with an unpacked PE file. BinText reveals some strings, but not URLs. Searching for HTTP with XORSearch (version 1.1) doesn’t reveal any XOR […]
Pingback by Reversing ROL-1 Malware « Didier Stevens — Sunday 16 September 2007 @ 7:16
[…] Stevens @ 7:57 Maarten Van Horenbeecks’s post gave me the idea for a new feature for my XORSearch tool: searching for a list of strings. This is achieved with the -f option, like […]
Pingback by XORSearch V1.3.0 « Didier Stevens — Wednesday 16 January 2008 @ 7:58
[…] updated my XORSearch tool to support ROT encoding. Comments […]
Pingback by Update: XORSearch V1.4.0 « Didier Stevens — Sunday 19 April 2009 @ 16:43
Hi Didier. Great program xorsearch is. I was curious if there is a linux compatible version out there.
Thanks!
Comment by Mike — Monday 20 April 2009 @ 18:23
Yes, I use it on Linux too. You just have to compile it: gcc -o XORSearch XORSearch.c
Comment by Didier Stevens — Monday 20 April 2009 @ 18:27
Does it support Unicode text in addition to ASCII? That would be a great feature!
Comment by MarkF — Saturday 12 December 2009 @ 1:59
No, it doesn’t, but it’s a good idea.
Comment by Didier Stevens — Sunday 13 December 2009 @ 17:49
Hello,
I tried out XORSearch and it found lots of neat stuff in chm and pdf files.
One thing I searched for was “.exe” but I discovered there’s no quick way to see text before the found text. Seems like a useful option may be to show N bytes after the found text but also some number of bytes before the text. It would be handy in not having to open each file in a hex editor and jump to the location and try to decode around that spot.
Great tool. I hope you might think of adding this option sometime.
BTW Using a linux gcc version here.
Thanks.
Comment by Chris S. — Tuesday 12 January 2010 @ 14:34
hello,
how to find xor key in pdf file which is 256 bye . any one help me .
Comment by san — Wednesday 21 April 2010 @ 10:59
[…] oprogramowania: upx, packerid, bytehist, xorsearch, […]
Pingback by » REMnux — programy do analizy złośliwego oprogramowania -- Niebezpiecznik.pl -- — Monday 12 July 2010 @ 9:15
[…] with protected executables: upx, packerid, bytehist, xorsearch, […]
Pingback by Malware Analysis Tools Set Up for Linux « Wikihead's Blog — Saturday 17 July 2010 @ 9:31
[…] objdump, Radare, shellcode2.exe Detección de protecciones y cifrados: upx, packerid, bytehist, xorsearch, TRiD. Análisis de PDF maliciosos: Didier’s PDF tools, Origami framework, Jsunpack-n, pdftk. […]
Pingback by REMnux, Distribución de Linux para el Análisis e Ingeniería Inversa de Malware | SinapsysMx.Net — Tuesday 20 July 2010 @ 14:00
[…] objdump, Radare, shellcode2.exe Detección de protecciones y cifrados: upx, packerid, bytehist, xorsearch, TRiD. Análisis de PDF maliciosos: Didier’s PDF tools, Origami framework, Jsunpack-n, pdftk. […]
Pingback by REMnux, Distribución de Linux para el Análisis e Ingeniería Inversa de Malware | Laboratorio de Seguridad y Hacking — Tuesday 20 July 2010 @ 15:36
[…] Radare, shellcode2.exe Detección de protecciones y cifrados: upx, packerid, bytehist, xorsearch, TRiD. Análisis de PDF maliciosos: Didier’s PDF tools, Origami framework, Jsunpack-n, […]
Pingback by REMnux, Distribución de Linux para el Análisis e Ingeniería Inversa de Malware | Command Line — Tuesday 20 July 2010 @ 16:05
[…] objdump, Radare, shellcode2.exe Detección de protecciones y cifrados: upx, packerid, bytehist, xorsearch, TRiD. Análisis de PDF maliciosos: Didier’s PDF tools, Origami framework, Jsunpack-n, pdftk. […]
Pingback by REMnux, Distribución de Linux para el Análisis e Ingeniería Inversa de Malware | Shadow Security — Wednesday 21 July 2010 @ 8:50
[…] objdump, Radare, shellcode2.exe Detección de protecciones y cifrados: upx, packerid, bytehist, xorsearch, TRiD. Análisis de PDF maliciosos: Didier’s PDF tools, Origami framework, Jsunpack-n, pdftk. […]
Pingback by Marcosof Informatica y Telecomunicaciones » Blog Archive » REMnux, Distribución de Linux para el Análisis e Ingeniería Inversa de Malware Leer más: Noticias de Seguridad Informática – Segu-Info: REMnux, Distribución de Linux para e — Thursday 22 July 2010 @ 5:16
[…] de protecciones y cifrados: upx, packerid, bytehist, xorsearch, […]
Pingback by REMnux – Distribución de Linux para el Análisis e Ingeniería Inversa de Malware | Tux Files — Saturday 24 July 2010 @ 3:51
[…] […]
Pingback by REMnux: A Linux Distribution for Reverse-Engineering Malware — Sunday 25 July 2010 @ 4:03
Do you know of a program (or have a 010 Editor script, or FileInsight plugin) that starts with an obfuscated string portion like nddgqwythy.net and applies those Hex Modifications XOR, ROL, and ROT in sequence, so we can spot the original string by eye?
Would adding binary add to XORSearch be useful?
Comment by Anonymous — Sunday 5 December 2010 @ 19:35
@Anonymous So you want to see each transformation so you can select the one that makes sense to you? No, don’t know such a program.
I could add binary add, but this would double the execution time of XORSearch.
Comment by Didier Stevens — Sunday 5 December 2010 @ 21:16
The idea would be to watch as the 010 Hex Operations (or the Decode tab in FileInsight) steps through adding binary 1, e.g.:
nddgqwythy -> oeehrxzuiz -> pffisy{vj{ and onward.
Then all the XOR keys (0 to 255) that XORSearch tries, e.g.:
nddgqwythy -> oeefpvxuix -> lffesu{vj{ and onward.
And the ROL/ROR transforms that XORSearch does.
Ideally it would dump these to a list that could be inspected to find the “real” string that has been obfuscated.
Comment by K P — Monday 6 December 2010 @ 2:49
[…] can carve them out manually. Didier Steven’s XORSearch and a hex editor should […]
Pingback by CVE-2012-0158 – South China Sea, Insider Information and other samples and analysis | DKbox — Sunday 12 August 2012 @ 3:02
thnx for sharing
Comment by raef — Monday 3 September 2012 @ 6:12
[…] XORSearch is one of my popular tools, but I hadn’t made a video for it yet: Like this:LikeBe the first to like this. Leave a Comment […]
Pingback by XORSearch Video « Didier Stevens — Wednesday 10 October 2012 @ 17:41
[…] tool written by Didier that I find useful is for analyzing shellcode is XORSearch. It’s basically a small light weight application that will try to brute force shellcode […]
Pingback by sudosecure.net » Blog Archive » Analyzing PDF files and Shellcode — Thursday 18 October 2012 @ 16:39
To compile on Mac you first need to apply the following patch as malloc.h is a deprecated import.
— XORSearch.c 2012-10-29 10:25:26.000000000 +0100
+++ XORSearch.c.ori 2010-01-17 10:57:24.000000000 +0100
@@ -28,9 +28,7 @@
#include
#include
#include
-#if !defined(__APPLE__)
#include
-#endif
#include
#include
#include
Comment by Christophe Vandeplas — Monday 29 October 2012 @ 9:28
@Christophe Yup, I Tweeted about it a couple of weeks ago.
And you can just drop the line with malloc.h, you don’t need conditional compilation.
Works fine on Windows and Linux too.
Comment by Didier Stevens — Monday 29 October 2012 @ 18:38
[…] Malware Analysis Essentials using REMnux webcast, during which he demonstrated the ‘xorsearch‘ command. This command will search for an xored version of a given string by, I believe, […]
Pingback by Where’s char *wally?: Searching for Strings in Single Byte Xor Encrypted Data « Malware Musings — Tuesday 30 October 2012 @ 21:45
[…] Update: there is another interesting project: https://blog.didierstevens.com/programs/xorsearch […]
Pingback by XOR em arquivos binarios | Alan Carvalho de Assis — Wednesday 7 November 2012 @ 13:44
[…] You can find the new version on XORSearch’s page. […]
Pingback by XORSearch for OSX « Didier Stevens — Thursday 8 November 2012 @ 21:59
[…] narzędzie, teraz także na OS […]
Pingback by » * XOR search -- Niebezpiecznik.pl -- — Tuesday 13 November 2012 @ 7:21
[…] go through the trouble if a single-byte XOR key can easily be bruteforced? Tools such as Didier Steven’s XORsearch do the job fine. The nice thing about this technique is that it can be extended to multi-byte […]
Pingback by unXOR - recover plaintext and key from XORed data | tomchop[is].me — Sunday 30 December 2012 @ 12:03
[…] new version of XORSearch comes with a new operation: shifting […]
Pingback by Update XORSearch V1.8.0: Shifting « Didier Stevens — Wednesday 20 February 2013 @ 21:33
[…] in search of a particular string. One popular tool available on both UNIX and Window platforms is XORSearch written by Didier Stevens. This tool searches for strings encoded in multiple formats, including […]
Pingback by Obfuscation: Malware’s best friend | Malwarebytes Unpacked — Friday 8 March 2013 @ 16:59
[…] is best described as the combination of my XORSearch tool and the well-known strings […]
Pingback by New Tool: XORStrings | Didier Stevens — Monday 15 April 2013 @ 0:01
[…] been asked many times to support 32-bit keys with my XORSearch tool. But the problem is that a 32-bit bruteforce attack would take too much […]
Pingback by Update: XORSearch Version 1.9.1 | Didier Stevens — Monday 14 October 2013 @ 5:00
[…] new version of XORSearch integrates Frank Boldewin’s shellcode detector. In his Hack.lu 2009 presentation, Frank […]
Pingback by Update: XORSearch With Shellcode Detector | Didier Stevens — Monday 29 September 2014 @ 0:00
[…] set of rules derived from Frank Boldewin’s OfficeMalScanner signatures, that I also use in my XORSearch program. Their goal is to find shellcode embedded in […]
Pingback by YARA Rules | Didier Stevens — Tuesday 16 December 2014 @ 0:00
[…] obfuscated or encrypted data with “xorsearch”, “findaes”, “xortool“, “aeskeyfind” and […]
Pingback by REMnux Usage Tips for Malware Analysis on Linux — Thursday 15 January 2015 @ 3:10
[…] Handle, DebugView, Autoruns, RKU, Kernel Detective, Malzilla, ExeInfo, PEStudio, Dependency Walker, XORSearch, SWFTools, Java Decompiler, […]
Pingback by Building Ultimate Anonymous Malware Analysis | iTeam Developers — Monday 2 February 2015 @ 17:02
[…] unXOR, XORStrings, ex_pe_xor, XORSearch, brutexor/iheartxor, xortool, NoMoreXOR, […]
Pingback by REMnux: Distribución de Linux especializada en en el análisis de malware | Skydeep — Thursday 20 August 2015 @ 1:49
[…] on peut espérer que les auteurs du binaire ont utilisé un simple XOR et compter sur les outils XORsearch / XORstrings de Didier […]
Pingback by FLOSS : trouver des chaines de caractères cachées dans un exécutable | .:[ d4 n3wS ]:. — Monday 4 July 2016 @ 15:31
[…] XORSearch & XORStrings – A couple programs from Didier Stevens for finding XORed data. […]
Pingback by Awesome Malware Analysis Lists – vulnerablelife — Wednesday 3 August 2016 @ 18:27
[…] been developing a new Python program similar to XORSearch. decoder-search.py does brute-forcing and searching of a file like XORSearch, but it stead of […]
Pingback by decoder-search.py Beta | Didier Stevens — Wednesday 28 September 2016 @ 0:00
[…] 11. XORSearch […]
Pingback by Computo Forense y Hacking » 13 herramientas para desofuscar código para reversers — Friday 30 September 2016 @ 5:12
[…] efficient? Not sure.. Either way, if you don’t heavily use Didier’s tools you should. https://blog.didierstevens.com/programs/xorsearch/ All of his tools are gold, and he is one productive […]
Pingback by Cozy Bear unique Drop Method – penetrate.io — Saturday 12 November 2016 @ 17:07
[…] these facts, one can use, for example, Didier Steven’s xorsearch to get the correct key and the resulting deobfuscated strings. The tool can be run on the ELF […]
Pingback by A short Addendum on the Mirai Botnet Blog Post – Insinuator.net — Thursday 8 December 2016 @ 13:04
[…] in search of a particular string. One popular tool available on both UNIX and Window platforms is XORSearch written by Didier Stevens. This tool searches for strings encoded in multiple formats, including […]
Pingback by Obfuscation: Malware’s best friend – vulnerablelife — Friday 6 January 2017 @ 7:26
[…] XORSearch […]
Pingback by SANs FOR610 Toolset | neilrobb.co.uk — Thursday 23 March 2017 @ 20:33
[…] xorsearch Locate and decode strings obfuscated using common techniques remnux-didier (APT) https://blog.didierstevens.com/programs/xorsearch/ Extract and Decode Artifacts: Deobfuscate XORStrings xorstrings Locate and decode XOR-obfuscated […]
Pingback by Remnux-A tool for reverse engineering Malware – Infohub — Saturday 8 April 2017 @ 22:41
[…] XORSearch & XORStrings – A couple programs from Didier Stevens for finding XORed data. […]
Pingback by Most Important Tools and Resources For Security Researcher, Malware Analyst, Reverse Engineer – My (Yet Another) Cybersecurity Blog — Wednesday 28 February 2018 @ 8:13
[…] encoded with various keys to see if any match up or decode the rest of the file. This is how Didier Steven’s xorsearch tool works. This could have worked here, but you would have to have a really good […]
Pingback by Cracking the DerbyCon Code - TrustedSec — Wednesday 18 September 2019 @ 12:45
[…] This means that the .bin file is likely shell code. To decode the binary, we will be using the tool XORsearch.exe. From the website: […]
Pingback by Crimson Rat (02-24-2020): VelvetSweatshop and shellcode – Click All the Things! — Thursday 27 February 2020 @ 12:54
On virustotal file XORSearch.exe is detected as trojan or mailware with many engines. It’s true or false positive?
Comment by Ramil — Saturday 11 April 2020 @ 20:44
I can’t answer this question if you don’t tell me which EXE exactly on VT you are referring to. My software is not malware, but you might have a version that I didn’t create.
Comment by Didier Stevens — Saturday 11 April 2020 @ 22:53
download software from this page https://didierstevens.com/files/software/XORSearch_V1_11_3.zip and upload to VT
and result is
https://www.virustotal.com/gui/file/50d1cdf5fe93e29e1d7fcb3cf2256ceac0034cbd887e4dac1cb897e14b28bc16/relations
Comment by Ramil — Sunday 12 April 2020 @ 15:25
Indeed, false positives.
Comment by Didier Stevens — Tuesday 14 April 2020 @ 7:33
@Didier Stevens Thank you for your tools. I just want to report that the current link to download XORSearch (https://didierstevens.com/files/software/XORSearch_V1_11_3.zip) results in a 404 error.
Comment by nh — Thursday 9 July 2020 @ 22:10
Please take the time to read what I wrote about that 404 error!
Comment by Didier Stevens — Thursday 9 July 2020 @ 22:14
@Didier Stevens I’m sorry, I totally missed the line regarding the 404 error. Thank you for the tools.
Comment by nh — Friday 10 July 2020 @ 4:24
No problem! You’re welcome.
Comment by Didier Stevens — Friday 10 July 2020 @ 8:16
[…] oledump.py, xorsearch, […]
Pingback by Quick & Dirty Shellcode Analysis – CVE-2017-11882 – Didier Stevens Videos — Wednesday 9 March 2022 @ 11:03
[…] oledump.py, re-search.py, hex-to-bin.py, translate.py, xorsearch, […]
Pingback by VBA Maldoc & UTF7 (APT-C-35) – Didier Stevens Videos — Sunday 4 September 2022 @ 14:42