Microsoft’s Malware Protection Center has a blogpost on a version of Rovnix that uses its own TCP/IP stack.
I used Wireshark to capture the network traffic generated by this sample when it is executed in a VMware guest.
I ran the sample on a XP SP3 guest machine in VMware. The hostname is XPPROSP3 (this name will appear in the HTTP GET request).
The guest uses NAT.
I ran the Wireshark capture on my host machine on the VMware Virtual Ethernet Adapter.
I removed some traffic coming from my host machine (NetBIOS Name Service and DHCPv6 to be precise).
When I executed the sample on XPPROSP3, it rebooted after a few seconds.
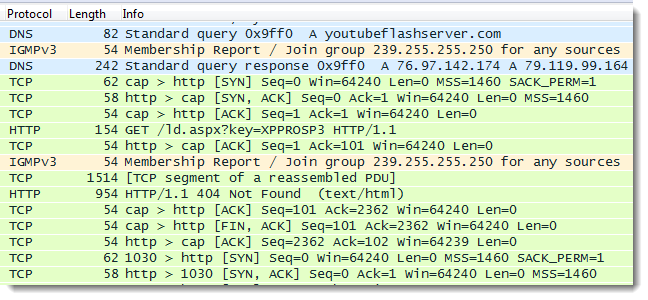
The trace:
The 37 second gap between packet 6 and 7 is due to the reboot of XPPROSP3
Packet 44: DNS request for youtubeflashserver
There are 3 HTTP requests. Notice User-Agent FWVersionTestAgent in all 3 GET requests.
Packet 50: first GET request with hostname XPPROSP3 as a parameter. Response: 404
Packet 61: second GET request, malformed. Response: 400
Packet 70: third GET request, malformed. Response: 400
rovnix-capture-filtered.zip (https)
MD5: C941D1716B6248C3FBFB4DFFA8AD2E86
SHA256: 51EDA61199DD9EDC1E50C5A9B5A4B69F32DB74E90CF098849554C56217D06EFD
Leave a Reply (comments are moderated)