Today I tested @Ivanlef0u ‘s .LNK PoC with my latest Ariad tool.
I adapted the PoC to work on a CD-ROM for drive D. When you load the CD-ROM with the PoC (I use an ISO file inside a VM) and take a look at DbgView’s output, you’ll notice that payload gets executed:
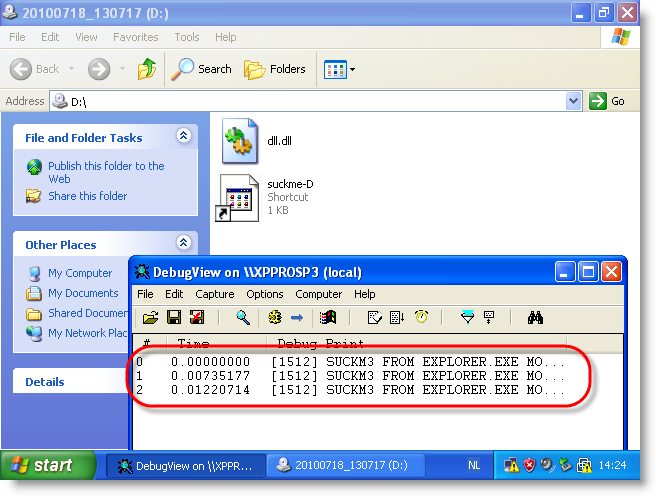
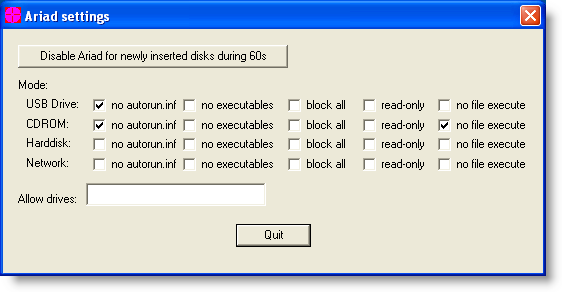
With Ariad installed on the machine in its default configuration (just block \autorun.inf), the PoC still works:
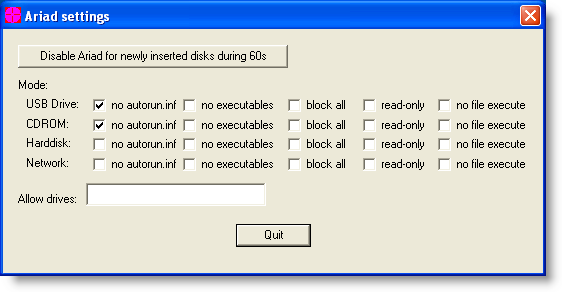
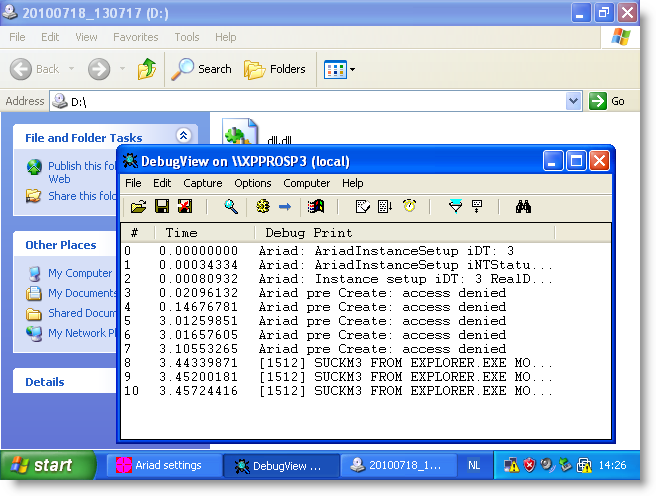
But configuring Ariad to block access to executables (this includes .LNK) prevents the PoC from executing:
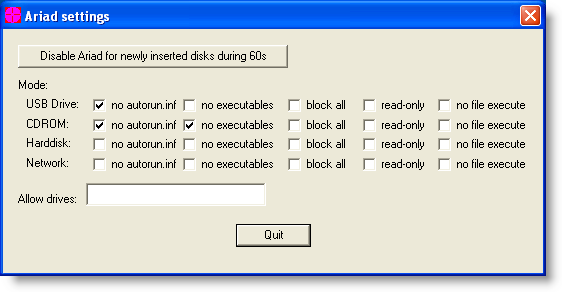
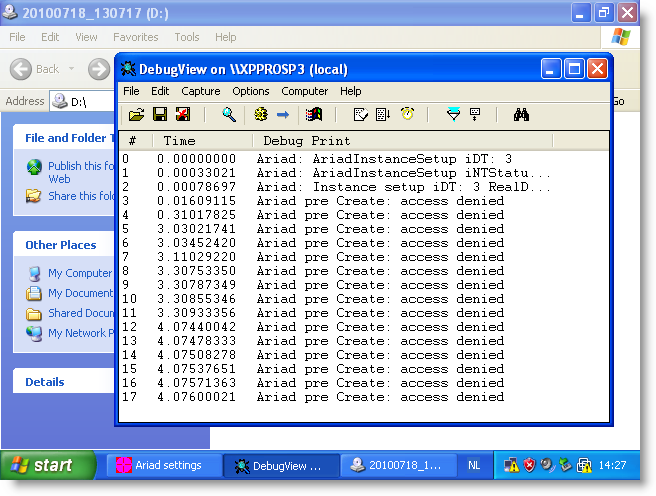
Access to the .LNK file is denied, and Windows Explorer can’t start the payload.
And configuring Ariad to prevent files to be mapped in memory (this is something done by Windows with executables) also prevents the PoC from executing:

This time, access to the .LNK file is not denied, but dll.dll is prevented from loading into memory, thus again preventing the payload from executing.
You can use Ariad if you want to mitigate attacks with these shortcut links until Microsoft releases a patch. As it is expected that Microsoft will not release a patch for Windows XP SP2, Ariad can offer permanent mitigation.
Be sure to read Ariad‘s documentation before using it.
Yo,
Thx for testing dude 🙂
Btw have you tried the workaround ‘Disable the displaying of icons for shortcuts’ from http://www.microsoft.com/technet/security/advisory/2286198.mspx ? You have to remove the registry entry ‘HKEY_CLASSES_ROOT\lnkfile\shellex\IconHandler’. Guess after this all your icons are not displayed lol …
Comment by Ivanlef0u — Sunday 18 July 2010 @ 13:58
@IvanLef0u Avec plaisir 😉 I’ll test this registry setting after I complete the documentation for Ariad.
Comment by Didier Stevens — Sunday 18 July 2010 @ 14:02
@ivan: most users let icon handler with default value.
@didier: nice experiment. keep it run,, bro!
Comment by Milo Rambaldi — Sunday 18 July 2010 @ 14:10
[…] Tutorial: 1. Unzip the files in ‘C: ’. Start a DbgView or paste a Konsole Debug to your Virtual Machine. 2. Rename ’suckme.lnk_’ to ’suckme.lnk’ and let the magic do the rest of shell32.dll. 3. Look at your logs,, can be like this. […]
Pingback by Prevent Microsoft Windows Automatic .lnk Shortcut File Code Execution | KompiError.com — Sunday 18 July 2010 @ 14:29
[…] Dider Stevens explique sur son blog comment l’outil qu’il a développé (Ariad) permet aussi de se protéger contre cette attaque. […]
Pingback by Faille de sécurité des raccourcis sous Windows « Criminalités numériques — Sunday 18 July 2010 @ 14:56
I wish I could use this in production env.. for now no icons in lnk’s
@Didier: btw it’s not just xp sp2 support that stopped, also win2k workstation. Talk about irony: the exploit was found first in malware that was designed to spy on scada aka wincc systems. A siemens implementation that runs mostly on.. you guessed it.
bonarez
Comment by bonarez — Sunday 18 July 2010 @ 17:05
@bonarez I know about win2k, and I believe my driver could run on it, but have not tested yet.
Comment by Didier Stevens — Sunday 18 July 2010 @ 17:06
Hi, the POC didn’t “seem” to work when i tried it ? Any chance you could comment in here http://www.wilderssecurity.com/showthread.php?s=df9a732a11b0ff29bf815cb38bb410b1&p=1714178#post1714178
TIA
CloneRanger
Comment by CloneRanger — Monday 19 July 2010 @ 2:19
@CloneRanger The link doesn’t work. Did you test it in the root of drive C: ? The LNK file contains a reference to c:\dll.dll
Comment by Didier Stevens — Monday 19 July 2010 @ 7:43
[…] Mitigating .LNK Exploitation With Ariad – didierstevens.com When you load the CD-ROM with the PoC (I use an ISO file inside a VM) and take a look at DbgView’s output, you’ll notice that payload gets executed. […]
Pingback by Week 28 in Review – 2010 | Infosec Events — Monday 19 July 2010 @ 9:57
Well it looks like it worked but only after interaction — like f2(rename)+enter,right click.properties —
but on “View” nothing (i changed view modes etc still nothing). Anyone having problems with this too?
Maybe original had those 4-5 LNK files for some purpose? Havent tried that approach yet.
(use your own DLL with some MsgBox() in DLLMAIN … more easy — you will get 3x popup ask Didier to explain why, he is smart one here anyway 😉 )
ps. Didier you run best blawg around 😛 atleast one with best comments section ^^
Comment by Derr — Monday 19 July 2010 @ 9:57
[…] ويندوز إكس بي حزمة الخدمات الثانية فإن باحثا أمنية قام بتجربة شفرة الهجوم على أداة أمنية تحمل إسم Ariad تعمل على إيقاف بعض من عمليات التشغيل التلقائي او تنفيذ […]
Pingback by ثغرة أمنية في ملفات الإختصارات الخاصة بويندوز | تيدوز — Monday 19 July 2010 @ 12:59
[…] ويندوز إكس بي حزمة الخدمات الثانية فإن باحثا أمنية قام بتجربة شفرة الهجوم على أداة أمنية تحمل إسم Ariad تعمل على إيقاف بعض من عمليات التشغيل التلقائي او تنفيذ […]
Pingback by ثغرة أمنية في نظام ملفات الإختصارات الخاصة بويندوز | إلكتروني — Monday 19 July 2010 @ 13:47
[…] Stevens also announced that he’d tested Ivanlef0u’s exploit against a tool he’d written a year ago, and said that the utility successfully blocked attacks launched from USB flash drives and CDs. “You can use Ariad if you want to mitigate attacks with these shortcut links until Microsoft releases a patch,” Stevens said of the tool in a Sunday blog. […]
Pingback by Windows ‘shortcut’ attack code goes public | Hack In The Box | Hacking and Computer security news — Monday 19 July 2010 @ 14:50
[…] Stevens also announced that he’d tested Ivanlef0u’s exploit against a tool he’d written a year ago, and said that the utility successfully blocked attacks launched from USB flash drives and CDs. “You can use Ariad if you want to mitigate attacks with these shortcut links until Microsoft releases a patch,” Stevens said of the tool in a Sunday blog. […]
Pingback by Windows ‘shortcut’ attack code goes public | IT Security, Hacking, Vulnerability alerts, IT Leadership and more — Monday 19 July 2010 @ 14:55
[…] ويندوز إكس بي حزمة الخدمات الثانية فإن باحثا أمنية قام بتجربة شفرة الهجوم على أداة أمنية تحمل إسم Ariad تعمل على إيقاف بعض من عمليات التشغيل التلقائي او تنفيذ […]
Pingback by ثغرة أمنية في نظام ملفات الإختصارات الخاصة بويندوز « ARAB LIBRARIANS — Monday 19 July 2010 @ 15:18
[…] From Didier Stevens: […]
Pingback by Mitigating .LNK Exploitation With Ariad - Donna's SecurityFlash — Monday 19 July 2010 @ 16:09
[…] […]
Pingback by Anonymous — Monday 19 July 2010 @ 17:22
I’ve tested this POC exploit against the following anti-malware mechanisms (so far):
SRP, Faronics Anti-Executable 2, COMODO Internet Security 4.1.150349.920, Online Armor Premium Personal Firewall v4.0.0.45, Malware Defender 2.7.1, Sandboxie 3.46, DefenseWall 3.04, GeSWall 2.9 Professional, Returnil System Safe 2011 RC (anti-executable component), AppGuard 1.4.7
http://ssj100.fullsubject.com/security-f7/vulnerability-in-windows-shell-could-allow-remote-code-execution-t187.htm#1303
Any requests?
Comment by ssj100 — Monday 19 July 2010 @ 20:15
[…] effective defenses. Didier Stevens has done this by testing his own Ariad tool on it and…. Ariad is a minifilter driver which blocks specific classes […]
Pingback by Exploit Code For Windows .LNK Flaw Public | Computer Security Articles — Monday 19 July 2010 @ 20:50
[…] these shortcut links until Microsoft releases a patch,” Stevens said of the tool in a Sunday blog […]
Pingback by Windows «shortcut» attack code goes public « The College of Arts and Sciences – Gathering Point for Technology at the University of Oregon — Monday 19 July 2010 @ 23:49
[…] these shortcut links until Microsoft releases a patch,” Stevens said of the tool in a Sunday blog […]
Pingback by Windows ‘Shortcut’ Attack Code Goes Public | Find Tech News — Tuesday 20 July 2010 @ 0:52
@ Didier Stevens
Yes i put dll.dll in c:\dll.dll as well as trying the POC from my USB stick. Still didn’t work ?
Please see in here for my tests with it, including using DbgView.exe to view the attempt – http://www.wilderssecurity.com/showthread.php?t=276994&page=5
TIA
Comment by CloneRanger — Tuesday 20 July 2010 @ 3:05
[…] https://blog.didierstevens.com/2010/07/18/mitigating-lnk-exploitation-with-ariad/ Third party software. […]
Pingback by Stuxnet – Surf wisely, stop clicking on anything you see! « TTC Shelbyville – Technical Blog — Tuesday 20 July 2010 @ 3:58
@CloneRanger In my VM tests, I noticed the PoC often ran only once. I had to rollback before testing again.
Comment by Didier Stevens — Tuesday 20 July 2010 @ 5:29
@CloneRanger As Didier Stevens has already mentioned, I’ve also noticed the POC often only runs once. Hence the beauty of creating snapshots in a VM! Also, in that Wilders thread, I note you tested PE Guard (version 1) and confused many people including aigle into thinking that PE Guard manages to block this POC – it doesn’t.
My favourite way to block this POC/malware has got to be SRP/AppLocker because they don’t involve any third party solutions (and they are also default deny).
Comment by ssj100 — Tuesday 20 July 2010 @ 6:23
[…] several people have suggested using SRP to protect against .LNK exploitation as an alternative to Ariad, I’ll describe how to configure SRP for the first time on a workstation that is not a member […]
Pingback by Mitigating .LNK Exploitation With SRP « Didier Stevens — Tuesday 20 July 2010 @ 7:13
Didier,
Is windows xp sp2 also affected for this vulnerability?
Thx!
Comment by Dft — Tuesday 20 July 2010 @ 8:15
@Dft Yes, and Windows 2000 too.
Comment by Didier Stevens — Tuesday 20 July 2010 @ 8:34
[…] ويندوز إكس بي حزمة الخدمات الثانية فإن باحثا أمنية قام بتجربة شفرة الهجوم على أداة أمنية تحمل إسم Ariad تعمل على إيقاف بعض من عمليات التشغيل التلقائي او تنفيذ […]
Pingback by انفديا - ثغرة أمنية في نظام ملفات الإختصارات الخاصة بويندوز — Tuesday 20 July 2010 @ 9:26
[…] XP SP2 and Upgrade to SP3 is not an option. You should read the blog of Didier Stevens at: Didier Steven’s Blog on using the ARAID Utility to protect XP SP2. Posted in ALERT – Virus, Security & Compliance | Tags: auto run, autorun.inf, cd, exploit, […]
Pingback by LNK vulnerability exploit | Tech II Business Services — Tuesday 20 July 2010 @ 12:55
[…] SRP to protect against .LNK exploitation as an alternative to Ariad, I’ll describe how to configure SRP for […]
Pingback by Mitigating .LNK Exploitation With SRP | Computer Security Articles — Tuesday 20 July 2010 @ 18:25
@Didier Stevens
Hi, it didn’t even seem to run even once, whatever i tried ?
@ssj100
Hi,
Re – PE Guard. Really ! I allowed it anyway, but still nothing ?
Nice tests of yours, good to see you’re still around, and now you’re da boss, lol.
Comment by CloneRanger — Tuesday 20 July 2010 @ 21:16
@CloneRanger Thanks, it’s all for fun really. I don’t see myself as much of a “boss” haha. By the way, did you follow my instructions of testing the POC here?:
http://ssj100.fullsubject.com/security-f7/vulnerability-in-windows-shell-could-allow-remote-code-execution-t187.htm#1308
I don’t know why it’s not working for you. What exactly is your testing environment? Ideally, you should be testing it on a freshly installed Windows. Cheers.
Comment by ssj100 — Tuesday 20 July 2010 @ 23:08
@CloneRanger Also, perhaps you should reply to aigle’s claim that PE Guard blocks the exploit – it does not.
Comment by ssj100 — Wednesday 21 July 2010 @ 0:05
[…] will also help researchers and users to provide effective defenses. Didier Stevens has done this by testing his own Ariad tool on it and confirming that it blocks the exploit. Ariad is a minifilter driver which blocks specific classes of files, now including .LNK files, […]
Pingback by Exploit Code For Windows .LNK Flaw Public- The Hackers Edge — Wednesday 21 July 2010 @ 1:49
[…] This Workaround” heading.Further reading:Siemens: German Customer Hit by Industrial WormMitigating Link Exploitation with AriadICS-CERT: USB Malware Targeting Siemens Control Software (PDF) var addthis_append_data='false';var […]
Pingback by Tool Blunts Threat from Windows Shortcut Flaw — Krebs on Security — Wednesday 21 July 2010 @ 5:24
[…] the displaying of icons for shortcuts“. Another way to protect yourself is to use Didier Stevens’ tool Ariad […]
Pingback by Windows shortcut flaw go wild? « The FORWARD project blog — Wednesday 21 July 2010 @ 13:33
[…] l’utilisation de son logiciel Ariad qui permet de contrôler finement l’ouverture automatique de fichiers depuis les supports amovibles ou externes. […]
Pingback by Stuxnet / CPLink la situation ne s’arrange pas « Criminalités numériques — Wednesday 21 July 2010 @ 14:58
[…] the DLL couldn’t be registered. The Ariad filter software by Didier Stevens is also said to prevent .lnk files from executing malicious code on 32-bit Windows systems. However, the author explicitly […]
Pingback by .lnk vulnerability: Microsoft fix causes icon chaos | IT Security, Hacking, Vulnerability alerts, IT Leadership and more — Wednesday 21 July 2010 @ 19:16
[…] the DLL couldn’t be registered. The Ariad filter software by Didier Stevens is also said to prevent .lnk files from executing malicious code on 32-bit Windows systems. However, the author explicitly […]
Pingback by .lnk vulnerability: Microsoft fix causes icon chaos | Hack In The Box | Hacking and Computer security news — Wednesday 21 July 2010 @ 19:17
[…] Windows hole was publicly released over the weekend, and a tool to mitigate the attacks was then released by security researcher Didier […]
Pingback by Tech Reviews » Details of the first ever control system malware (FAQ) — Wednesday 21 July 2010 @ 19:53
Hi, did some more tests, and this time the POC succeeded.
Please see here for the details with screenies.
http://www.wilderssecurity.com/showthread.php?t=276994&page=7
Thanks
Comment by CloneRanger — Wednesday 21 July 2010 @ 20:19
@CloneRanger I see that to block the POC with ProcessGuard, you essentially block “rundll32.exe” from running. How practical is that for the majority of computer users? I can see a lot of (normal and safe) operations being broken by blocking “rundll32.exe”.
Anyway, nice to see you got the POC working. You seem to still be questioning whether PE Guard (versions 1 or 2) is able to block the POC. Why don’t you load up a freshly installed Windows, install PE Guard on it, and then do the test?
Comment by ssj100 — Wednesday 21 July 2010 @ 22:23
[…] that the DLL couldn't be registered. The Ariad filter software by Didier Stevens is also said to prevent .lnk files from executing malicious code on 32-bit Windows systems. However, the author explicitly […]
Pingback by UPDFATE (afain) .lnk vulnerability: Microsoft fix causes icon chaos — Thursday 22 July 2010 @ 10:39
Looks like the Windows world is learning about “mount -o noexec”. Not too soon!
Comment by Baptiste — Thursday 22 July 2010 @ 11:40
[…] approach to mitigate the possible LNK attack involves the use of Didier Stevens’ tool Ariad. Note that the tool is beta-software operating in the OS kernel, so it’s probably not a good […]
Pingback by How do I protect myself against the .LNK vulnerability? | Tech News — Thursday 22 July 2010 @ 17:24
@ssj100
Yes blocking “rundll32.exe” from running with ProcessGuard definately works. For most people it might not be practical ? What i can say is that, it hasn’t broken Anything for me, and i have NOT had ANY rundll32.exe alerts for Anything else. So it’s fine for me.
As for, installing a freshly installed Windows and testing PEG, i’m afraid i don’t have the time.
No i wasn’t “questioning whether PE Guard (versions 1 or 2) is able to block the POC” just wasn’t sure whether it remembered my allowing it or not. V1 is a bit naughty, sometimes it remembers, sometimes it doesn’t. I believe V2 is better in that respect, and more.
Comment by Anonymous — Thursday 22 July 2010 @ 17:43
@ssj100
Post 48 was from me CloneRanger, just wasn’t logged.
Comment by CloneRanger — Thursday 22 July 2010 @ 19:33
[…] used to create an effective malware attack on any Windows operating system.Stevens announced in a blog post that he had tested Ivanlef0u’s code using his self made tool and that the utility successfully […]
Pingback by Windows Shortcut Bug Code Made Public — Thursday 22 July 2010 @ 19:40
[…] блогозаписи (в конце её) рекомендовалось ознакомиться с советами во блоге независимого исслед… (по имени Didier Stevens), который рекомендовал вырубить […]
Pingback by Информационная безопасность / Уязвимость Microsoft Windows, которую демонстрировал 0-day exploit 19 июля, оказалась многовекторною: сайты могут автомат� — Thursday 22 July 2010 @ 21:42
@CloneRanger “rundll32.exe” is indeed required for many normal and safe operations – you just haven’t got round to issuing them just yet haha. Here are a few such normal operations that many people will use frequently:
1. Using “Open With” menu to choose the program you want to open a file with
2. Using “Safely Remove Hardware” so you can safely unplug a device from your computer
3. Opening “Date and Time Properties” (eg. so you can view the calender, adjust time/date)
4. Opening “System Properties” (eg. so you can change Performance options, enable/disable DEP)
5. Opening “Display Properties” (eg. so you can change desktop wallpaper, screensaver)
6. Opening “Add or Remove Programs” (eg. so you can uninstall programs)
7. Opening “Mouse Properties” (eg. so you can adjust the scrolling speed of your mouse)
8. Opening “Keyboard Properties” (eg. so you can adjust the cursor blink rate)
9. Opening “Sound and Audio Devices Properties” (eg. so you can change Windows Sound scheme)
10. Opening “Phone and Modem Options” (so you can add a phone/modem device)
Keep in mind that the above list applies only for Windows processes itself. I’m fairly sure many third party applications would also call “rundll32.exe”.
So yes, blocking “rundll32.exe” isn’t exactly very good advice for most people.
Comment by ssj100 — Thursday 22 July 2010 @ 23:49
And what if procedure in lnk file dont call malicious executable file (like dll.dll in this post)? What if it call some system procedures/commands? Does srp safe from that?
Comment by Mike Br. — Friday 23 July 2010 @ 9:48
Oh, and I’m a little bit shocked that no Wilders member has corrected your mis-information (no insult intended). You write:
***
“The best way i’ve found to stop this dead, is to have run32.dll (rundll32.exe) set to prompt, as i showed earlier when i tested the POC It’s not a cure as such, but that setting is staying on my comp with ProcessGuard”
***
However, not only would that be a bit impractical for many people, but it doesn’t actually stop the original exploit. Zero_One from BluePoint Security describes it well here:
http://ssj100.fullsubject.com/security-f7/vulnerability-in-windows-shell-could-allow-remote-code-execution-t187-15.htm#1390
***
“Double click call looks like shell32.dll -> explorer.exe -> rundll32.exe -> LoadLibraryW -> bad.dll
Browse looks like shell32.dll -> explorer.exe -> LoadLibraryW -> bad.dll”
***
As you can see, your method of blocking or prompting for every “rundll32.exe” process will only mitigate the exploit if it is executed via double clicking the shortcut file. It will NOT do anything against the original method of propagation (via simply browsing the infected file).
Zero_One also makes a good point here:
http://ssj100.fullsubject.com/security-f7/vulnerability-in-windows-shell-could-allow-remote-code-execution-t187-15.htm#1393
***
“Worse yet, blocking rundll only blocks the manual shortcut double click method. The browse method calls the loadlibrary api directly, so blocking rundll32.exe wouldn’t do any good of course. Unfotunately the browse by method is the most likely infection vector as well.”
***
Anyway, hope you get to read this. I would NOT recommend anyone to follow your method of blocking/prompting for every “rundll32.exe” instance – not only is it not effective, but it could break several normal and safe operations.
Comment by ssj100 — Friday 23 July 2010 @ 10:39
@Mike Br. If the LNK file doesn’t call a malicious file/process, what is there to worry about? The power of SRP/AppLocker is that any file that isn’t white-listed and tries to execute will be blocked. Therefore, SRP/AppLocker will (always) block any malcious process, no matter where it is called in the propagation.
Comment by ssj100 — Friday 23 July 2010 @ 10:44
@ssj100
Hi,
Quote
“rundll32.exe is indeed required for many normal and safe operations”
Indeed, but not very often on my comp, so i’m quite happy ONLY allowing it as and when required. As i said, it might not suit everybody, but it’s fine with me.
Quote
“As you can see, your method of blocking or prompting for every rundll32.exe process will only mitigate the exploit if it is executed via double clicking the shortcut file. It will NOT do anything against the original method of propagation (via simply browsing the infected file).”
Yes and no ! ONLY if dll.dll has already been placed in C:\ first manually. Please see Post 178 here – http://www.wilderssecurity.com/showthread.php?p=1717108#post1717108
Regards
Comment by CloneRanger — Saturday 24 July 2010 @ 14:10
[…] Windows zero-day exploit?: USB storage + .lnk files + file explorer = FAIL I just did a presentation to the State of Mississippi on USB as an attack vector. The vector continues to evolve.. I love it. … another tool for my kit! http://grandstreamdreams.blogspot.com/2010/07/windows-zero-day-exploit-usb-storage.html and https://blog.didierstevens.com/2010/07/18/mitigating-lnk-exploitation-with-ariad/ […]
Pingback by Windows zero-day exploit?: USB storage + .lnk files + file explorer = FAIL « Steve on Security — Sunday 25 July 2010 @ 22:25
@CloneRanger That’s fair enough if you don’t mind being prompted for every “rundll32.exe” related process. However, you’ve missed the point. Again, “rundll32.exe” wasn’t even required in the original exploit. The POC that was released is just an example of how a person plugging in a USB drive could get infected by simply browsing the files (and not double clicking on them).
Instead of C:\ (as in the case of the POC), the original actual malware used other drive letters (eg. F:\, G:\) that a USB drive would use. I’m sure you’ve read the news about the malware – you only need to browse the files to get infected, and this doesn’t require “rundll32.exe” to run. As my testing clearly shows, and Zero_One from BluePoint Security confirms, only explorer.exe is required to run for the infection to propagate:
***
shell32.dll -> explorer.exe -> LoadLibraryW -> bad.dll
***
Again, it’s unfortunate that no one on Wilders is making these points in reply to your post.
Comment by ssj100 — Monday 26 July 2010 @ 1:45
@ssj100
I think you are missing my points.
I was talking about my testing the POC, as shown on Wilders. Unless i copied dll.dll into C:\ it didn’t work.
Ran the real Stuxnet malware – http://www.wilderssecurity.com/showthread.php?s=a82d1decd29d44242b1675578a9ccfd3&t=276558
If you want to send me another version of the real Stuxnet i’ll test it from my USB stick. Someone will have to PM me at Wilders with a rapidshare etc link.
Comment by CloneRanger — Monday 26 July 2010 @ 21:09
@CloneRanger Let me break it down for you, as I’m indeed getting confused as to what point you’re trying to make:
1. You claim/imply/state that blocking or prompting for “rundll32.exe” is an effective means of mitigating the LNK exploit. In fact, I think you wrote that it’s the “best way”.
2. I reply that the exploit doesn’t even call “rundll32.exe”.
3. So if the exploit doesn’t use “rundll32.exe”, why would you want to block “rundll32.exe”?
Comment by ssj100 — Tuesday 27 July 2010 @ 1:50
[…] announced in a blog post that he had tested Ivanlef0u’s code using his self made tool and that the utility successfully […]
Pingback by Windows “Shortcut” Bug Code Made Public — Tuesday 27 July 2010 @ 2:08
[…] thing that I don't like about MS fix is that you loses the shortcun icon aesthetic. Sophos tool and Ariad are both good alternatives, but I personally chosed LUA/SRP to block this threat. Forget about MS […]
Pingback by Free_Sophos_tool_blocks_Windows_shortcut_attacks — Tuesday 27 July 2010 @ 9:59
Forget about MS? My friend, the fact that you are using LUA/SRP means that you are not forgetting about MS – you are using their very own tools to successfully mitigate this exploit.
Comment by ssj100 — Tuesday 27 July 2010 @ 21:07
And by the way, the Sophos tool isn’t reliable at all:
http://ssj100.fullsubject.com/security-f7/vulnerability-in-windows-shell-could-allow-remote-code-execution-t187-60.htm#1509
On the other hand, G Data appears to have fairly good method.
Comment by ssj100 — Tuesday 27 July 2010 @ 21:08
@ssj100
The following post is from July 21st, 2010, 04:03 PM You must have missed it ?
Tested the POC again today Post 158 – http://www.wilderssecurity.com/showthread.php?s=e552f5bdfcc2d68751a41d9f0a393206&t=276994&page=7
It shows what happened when i included, and removed run32.dll detection in ProcessGuard.
Comment by CloneRanger — Wednesday 28 July 2010 @ 2:50
@CloneRanger Sorry, but you’re still not understanding what I’m trying to tell you. “rundll32.exe” is only called when you double click the LNK file. However, it is not called when you just browse the files (which is the original exploit).
Please repeat your tests against the POC as described here (test A):
http://ssj100.fullsubject.com/security-f7/vulnerability-in-windows-shell-could-allow-remote-code-execution-t187.htm#1308
Hopefully now you will understand why blocking “rundll32.exe” does absolutely nothing against the original exploit. If you still disagree, then there’s nothing more I can do. You can ask someone professionally knowledgeable like EraserHW from Prevx for confirmation – he will agree with me, just like Zero_One from BluePoint Security did. In fact, I’m surprised Didier Stevens himself hasn’t commented on this – it’s his blog after all, and I would have thought his readers deserved clarification of any mis-information.
Comment by ssj100 — Wednesday 28 July 2010 @ 8:15
@ssj100
I see why you’re hung up over the rundll32.exe thingy !
I’m more concerned that UNLESS dll.dll is FIRST copied to C:\ NEITHER A or B test exploit works.
As i mentioned before, if you want to send me a version of the “REAL” Stuxnet i’ll test it LIVE from my USB stick. Someone will have to PM me at Wilders with a rapidshare etc link
C ya
Comment by CloneRanger — Thursday 29 July 2010 @ 3:37
@CloneRanger My friend, thanks for the reply. I’ll give it one last shot. You write:
***
“I’m more concerned that UNLESS dll.dll is FIRST copied to C:\ NEITHER A or B test exploit works.”
***
I don’t see why that would be relevant in the case of a USB device. When you plug in an infected USB device (eg. which ALREADY has the DLL file on it), you wouldn’t need to copy anything first.
Comment by ssj100 — Thursday 29 July 2010 @ 23:43
@ssj100
Ditto, You write:
“I don’t see why that would be relevant in the case of a USB device. When you plug in an infected USB device (eg. which ALREADY has the DLL file on it), you wouldn’t need to copy anything first.”
I have already posted at least TWICE,
“ONLY if dll.dll has already been placed in C:\ first manually. Please see Post 178 here – http://www.wilderssecurity.com/showthread.php?p=1717108#post1717108”
From my wilders post,
“I deleted dll.dll from C:\ and tried the POC again from both my USB stick and a folder on my desktop. This time just cruising and double clicking showed NO entry in DbgView ! = Fail”
Do remember i am talking about the POC !
Still no PM with a Real Stuxnet nasty for me to run and test and respond to ?
Have a nice weekend everybody
*
Comment by CloneRanger — Friday 30 July 2010 @ 23:34
[…] approach to mitigate the possible LNK attack involves the use of Didier Stevens’ tool Ariad. Note that the tool is beta-software operating in the OS kernel, so it’s probably not a good […]
Pingback by How do I protect myself against the .LNK vulnerability? | Blogs News — Thursday 5 August 2010 @ 13:24
[…] I’m writing this quickpost just in case you hadn’t figured this out for yourself: the techniques I described to protect machines from the .LNK vulnerability also help you mitigate the DLL […]
Pingback by Quickpost: Ariad & DLL Preloading « Didier Stevens — Thursday 26 August 2010 @ 12:11
Thanks a lot Sr. Didier Stevens,
I think Ariad will contribute a lot in the fight with an outbreak of LNK FLAW exploiting rootkit-virusses here in Juigalpa, Nicaragua.
gracias, Jan Willem
Comment by Jan Willem — Friday 29 October 2010 @ 23:24
[…] l’utilisation de son logiciel Ariad qui permet de contrôler finement l’ouverture automatique de fichiers depuis les supports amovibles ou externes. […]
Pingback by Stuxnet / CPLink la situation ne s’arrange pas | Linux-backtrack.com — Thursday 10 February 2011 @ 21:32
[…] approach to mitigate the possible LNK attack involves the use of Didier Stevens’ tool Ariad. Note that the tool is beta-software operating in the OS kernel, so it’s probably not a good […]
Pingback by How do I protect myself against the .LNK vulnerability? — Monday 7 March 2011 @ 7:43